Which of the following commands is used to monitor cluster members?
Correct Answer:A
You can see the following graphic: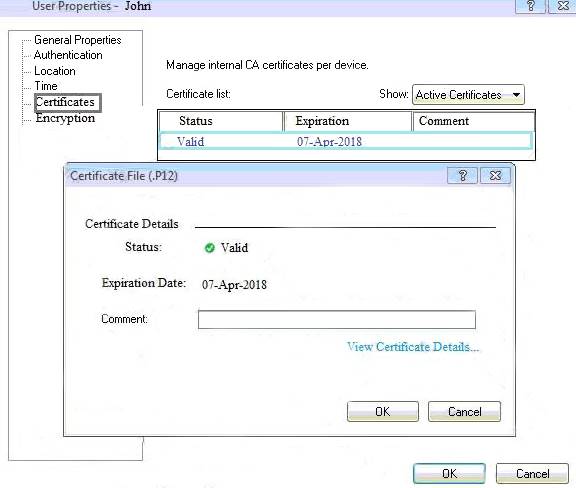
What is presented on it?
Correct Answer:A
An administrator wishes to enable Identity Awareness on the Check Point firewalls. However they allow users to use company issued or personal laptops. Since the administrator cannot manage the personal laptops, which of the following methods would BEST suit this company?
Correct Answer:B
Which policy type is used to enforce bandwidth and traffic control rules?
Correct Answer:D
https://sc1.checkpoint.com/documents/R80.30/WebAdminGuides/EN/CP_R80.30_QoS_AdminGuide/html_fram
Consider the Global Properties following settings: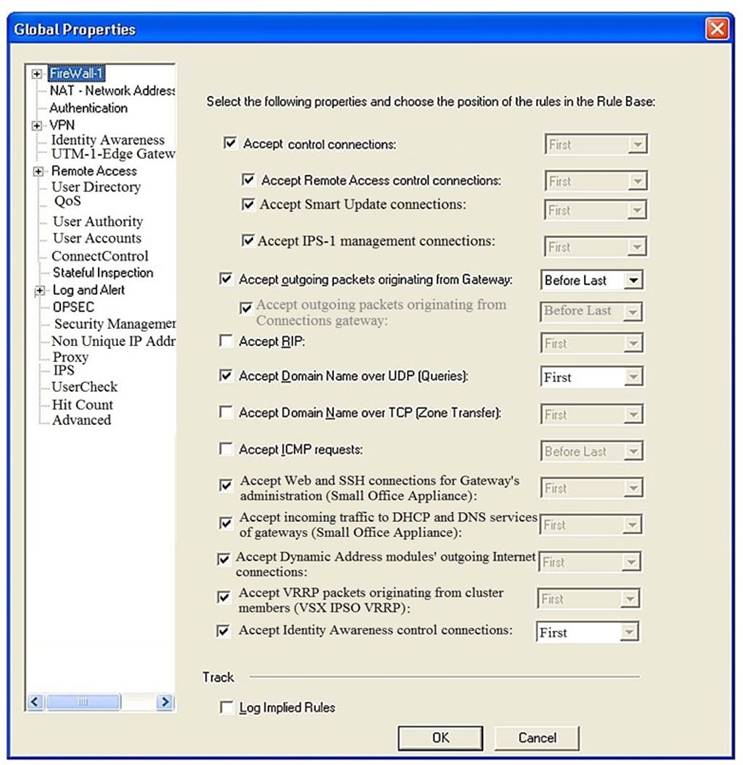
The selected option “Accept Domain Name over UDP (Queries)” means:
Correct Answer:A