Which security technique limits access by unauthorized users to parts of an enterprise database?
Correct Answer:A
Consider the symbols shown in the exhibit. Which of the following correctly identifies these symbols when used in an entity-relationship (ER) diagram?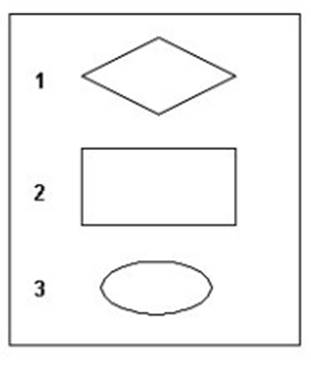
Correct Answer:C
Which type of relational integrity is violated if a primary key in a database has a null value?
Correct Answer:A
Which of the following best describes a composite key?
Correct Answer:D
Consider the entity-relationship (ER) diagram shown in the exhibit. Which type of relationship between the two entities is shown?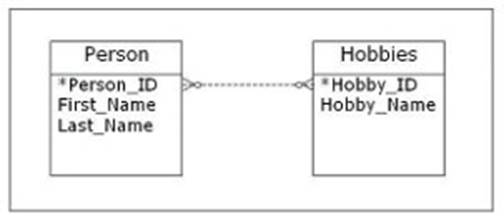
Correct Answer:B