Scenario: A Citrix Architect needs to design a new multi-datacenter NetScaler deployment. The customer wants NetScaler to provide access to various backend resources by using Global Server Load Balancing (GSLB) in an Active-Active deployment.
Click the Exhibit button to view additional requirements identified by the architect.
Which GSLB algorithm or method should the architect use for the deployment, based on the stated requirements?
Correct Answer:B
Reference: https://docs.citrix.com/en-us/netscaler/12/global-server-load-balancing/methods/configuring-algorithm-based-methods.html
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.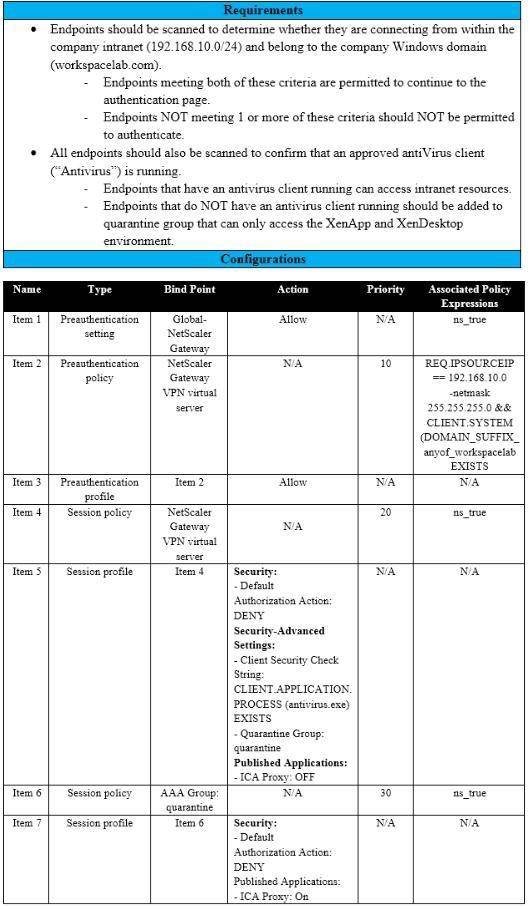
Which setting is preventing the security requirements of the organization from being met?
Correct Answer:F
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for NetScaler design project:
* The authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
* The workspacelab users connecting from the internal (workspacelab) network should be authenticated using LDAP.
* The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS.
* The vendorlab users should be authenticated using Active Directory Federation Service.
* The user credentials must NOT be shared between workspacelab and vendorlab.
* Single Sign-on must be performed between StoreFront and NetScaler Gateway.
* A domain drop down list must be provided if the used connects to the NetScaler gateway virtual server externally.
Which method must the architect utilize for user management between the two domains?
Correct Answer:B
Scenario: A Citrix Architect needs to assess an existing NetScaler gateway deployment. During the assessment, the architect collects key requirements for different user groups, as well as the current session profile settings that are applied to those users.
Click the Exhibit button to view the information collected by the architect.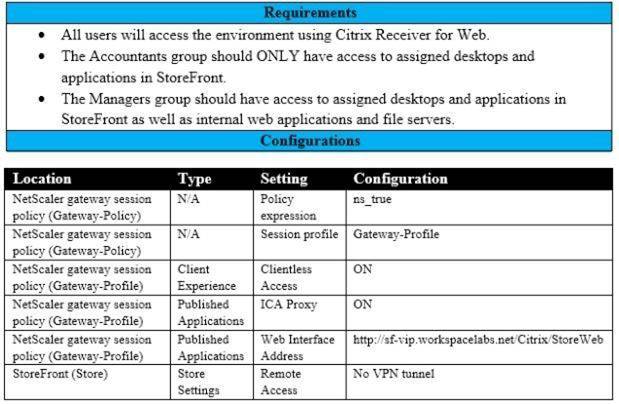
Which configuration should the architect make to meet these requirements?
Correct Answer:D
Scenario: A Citrix Architect needs to assess an existing NetScaler Gateway deployment. During the assessment, the architect collected key requirements for VPN users, as well as the current session profile settings that are applied to those users.
Click the Exhibit button to view the information collected by the architect.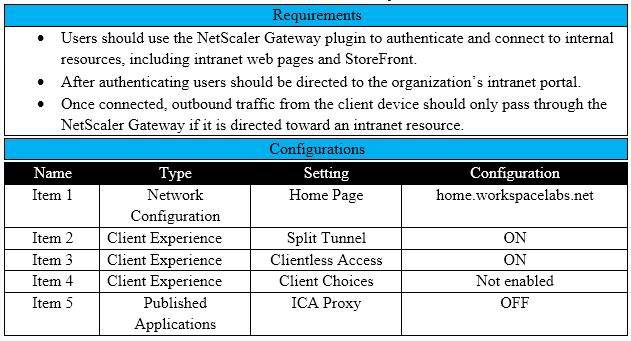
Which configurations should the architect change to meet all the stated requirements?
Correct Answer:E