No Installation Required, Instantly Prepare for the 200-201 exam and please click the below link to start the 200-201 Exam Simulator with a real 200-201 practice exam questions.
Use directly our on-line 200-201 exam dumps materials and try our Testing Engine to pass the 200-201 which is always updated.
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
Correct Answer:C
The target web application server is running as the root user and is vulnerable to command injection. Which result of a successful attack is true?
Correct Answer:B
Which access control model does SELinux use?
Correct Answer:C
Refer to the exhibit.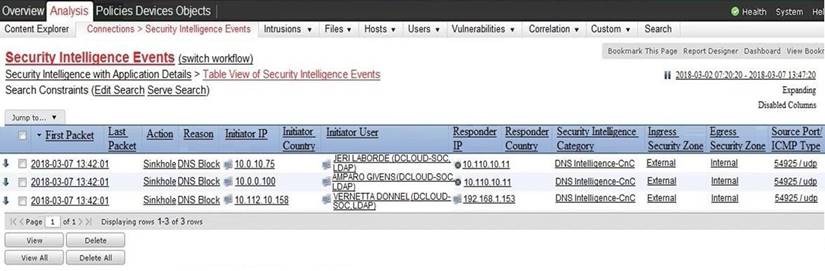
Which two elements in the table are parts of the 5-tuple? (Choose two.)
Correct Answer:DE
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
Correct Answer:C