A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
Correct Answer:A
What is the difference between a threat and a risk?
Correct Answer:A
Drag and drop the technology on the left onto the data type the technology provides on the right.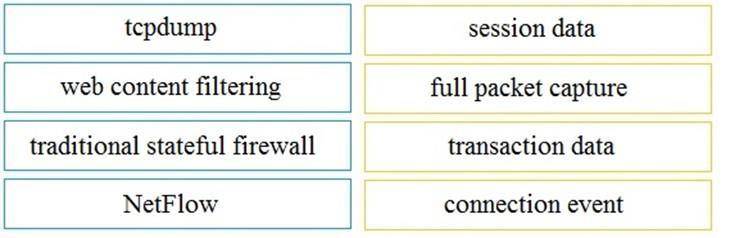
Solution: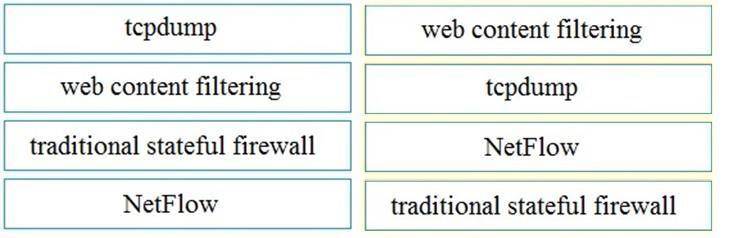
Does this meet the goal?
Correct Answer:A
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
Correct Answer:A
What is the virtual address space for a Windows process?
Correct Answer:D