In a SOC environment, what is a vulnerability management metric?
Correct Answer:D
Refer to the exhibit.
Which event is occurring?
Correct Answer:C
Refer to the exhibit.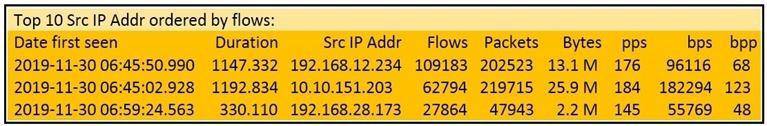
What information is depicted?
Correct Answer:B
What are the two characteristics of the full packet captures? (Choose two.)
Correct Answer:CE
Which step in the incident response process researches an attacking host through logs in a SIEM?
Correct Answer:A