Which two elements help to secure your API keys? (Choose two.)
Correct Answer:AC
ConfigMap keys have been mapped to different file names using the volumes.configMap.items field. What is the result if a wrong ConfigMap key is specified?
Correct Answer:A
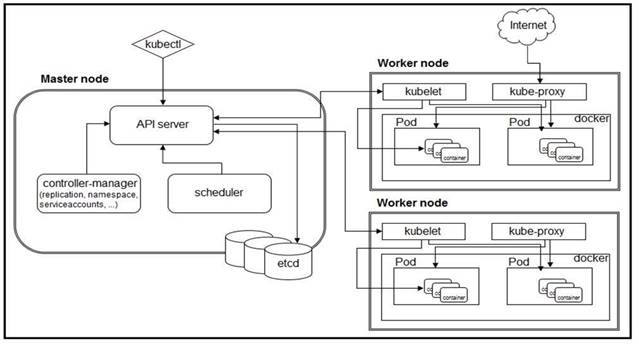
Refer to the exhibit. A developer needs to scale the existing pods within the worked nodes. Which object should be edited to achieve this goal?
Correct Answer:A
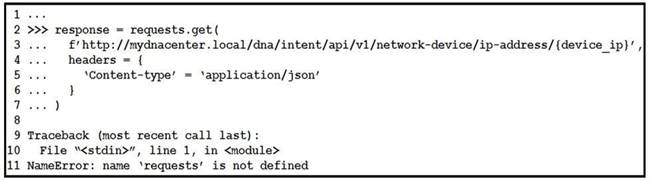
Refer to the exhibit. What is causing the requests code to fail?
Correct Answer:B
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
Correct Answer:AC