No Installation Required, Instantly Prepare for the 312-39 exam and please click the below link to start the 312-39 Exam Simulator with a real 312-39 practice exam questions.
Use directly our on-line 312-39 exam dumps materials and try our Testing Engine to pass the 312-39 which is always updated.
John, a threat analyst at GreenTech Solutions, wants to gather information about specific threats against the organization. He started collecting information from various sources, such as humans, social media, chat room, and so on, and created a report that contains malicious activity.
Which of the following types of threat intelligence did he use?
Correct Answer:D
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.
What does this event log indicate?
Correct Answer:A
What does [-n] in the following checkpoint firewall log syntax represents?
fw log [-f [-t]] [-n] [-l] [-o] [-c action] [-h host] [-s starttime] [-e endtime] [-b starttime endtime] [-u unification_scheme_file] [-m unification_mode(initial|semi|raw)] [-a] [-k (alert name|all)] [-g] [logfile]
Correct Answer:A
Which of the following tool is used to recover from web application incident?
Correct Answer:B
An organization is implementing and deploying the SIEM with following capabilities.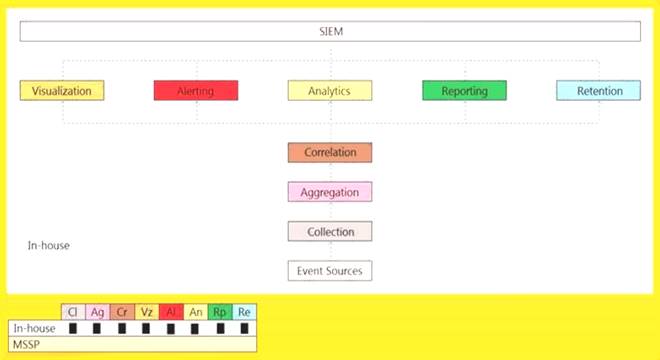
What kind of SIEM deployment architecture the organization is planning to implement?
Correct Answer:A