- (Exam Topic 2)
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.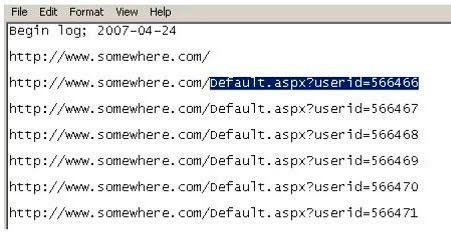
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
Correct Answer:A
- (Exam Topic 2)
Which of the following file contains the traces of the applications installed, run, or uninstalled from a system?
Correct Answer:A
- (Exam Topic 2)
What technique used by Encase makes it virtually impossible to tamper with evidence once it has been acquired?
Correct Answer:B
- (Exam Topic 3)
Adam, a forensic analyst, is preparing VMs for analyzing a malware. Which of the following is NOT a best practice?
Correct Answer:D
- (Exam Topic 1)
One technique for hiding information is to change the file extension from the correct one to one that might not be noticed by an investigator. For example, changing a .jpg extension to a .doc extension so that a picture file appears to be a document. What can an investigator examine to verify that a file has the correct extension?
Correct Answer:B