No Installation Required, Instantly Prepare for the 312-50 exam and please click the below link to start the 312-50 Exam Simulator with a real 312-50 practice exam questions.
Use directly our on-line 312-50 exam dumps materials and try our Testing Engine to pass the 312-50 which is always updated.
- (Topic 3)
A distributed port scan operates by:
Correct Answer:D
Think of dDoS (distributed Denial of Service) where you use a large number of computers to create simultaneous traffic against a victim in order to shut them down.
- (Topic 23)
Fake Anti-Virus, is one of the most frequently encountered and persistent threats on the web. This malware uses social engineering to lure users into infected websites with a technique called Search Engine Optimization.
Once the Fake AV is downloaded into the user's computer, the software will scare them into believing their system is infected with threats that do not really exist, and then push users to purchase services to clean up the non-existent threats.
The Fake AntiVirus will continue to send these annoying and intrusive alerts until a payment is made.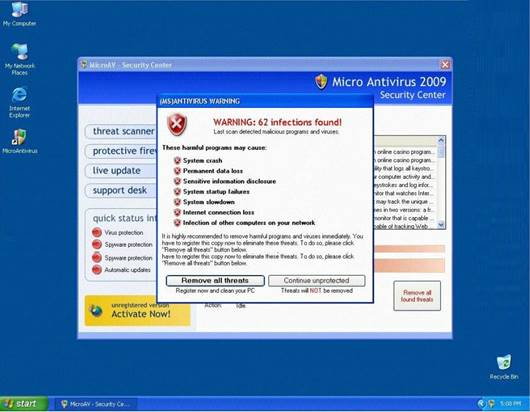
What is the risk of installing Fake AntiVirus?
Correct Answer:B
- (Topic 17)
What does the this symbol mean?
Correct Answer:A
This symbol is a “warchalking” symbol for a open node (open circle) with the SSID tsunami and the bandwidth 2.0 Mb/s
- (Topic 14)
Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
Correct Answer:B
SQL injection is a security vulnerability that occurs in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is in fact an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another.
- (Topic 6)
Assuring two systems that are using IPSec to protect traffic over the internet, what type of general attack could compromise the data?
Correct Answer:DE
To compromise the data, the attack would need to be executed before the encryption takes place at either end of the tunnel. Trojan Horse and Back Orifice attacks both allow for potential data manipulation on host computers. In both cases, the data would be compromised either before encryption or after decryption, so IPsec is not preventing the attack.