- (Topic 20)
A buffer overflow occurs when a program or process tries to store more data in a buffer (temporary data storage area) then it was intended to hold.
What is the most common cause of buffer overflow in software today?
Correct Answer:D
Technically, a buffer overflow is a problem with the program's internal implementation.
- (Topic 5)
In the context of Windows Security, what is a 'null' user?
Correct Answer:C
NULL sessions take advantage of “features” in the SMB (Server Message Block) protocol that exist primarily for trust relationships. You can establish a NULL session with a Windows host by logging on with a NULL user name and password. Using these NULL connections allows you to gather the following information from the host:* List of users and groups * List of machines * List of shares * Users and host SID' (Security Identifiers)
NULL sessions exist in windows networking to allow: * Trusted domains to enumerate resources * Computers outside the domain to authenticate and enumerate users * The SYSTEM account to authenticate and enumerate resources
NetBIOS NULL sessions are enabled by default in Windows NT and 2000. Windows XP and 2003 will allow anonymous enumeration of shares, but not SAM accounts.
- (Topic 23)
Lee is using Wireshark to log traffic on his network. He notices a number of packets being directed to an internal IP from an outside IP where the packets are ICMP and their size is around 65,536 bytes. What is Lee seeing here?
Correct Answer:C
- (Topic 14)
When a malicious hacker identifies a target and wants to eventually compromise this target, what would be among the first steps that he would perform? (Choose the best answer)
Correct Answer:C
A hacker always starts with a preparatory phase (Reconnaissance) where he seeks to gather as much information as possible about the target of evaluation prior to launching an attack. The reconnaissance can be either passive or active (or both).
- (Topic 23)
How do you defend against DHCP Starvation attack?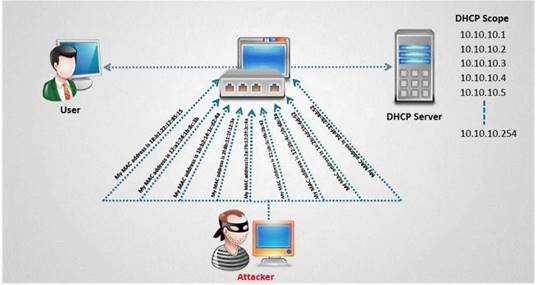
Correct Answer:B