- (Topic 13)
Which of the following is the best way an attacker can passively learn about technologies used in an organization?
Correct Answer:C
Note: Sending web bugs, webcrawling their site and port scanning are considered "active" attacks, the question asks "passive"
- (Topic 11)
Sara is making use of Digest Authentication for her Web site. Why is this considered to be more secure than Basic authentication?
Correct Answer:B
Digest access authentication is one of the agreed methods a web page can use to negotiate credentials with a web user (using the HTTP protocol). This method builds upon (and obsoletes) the basic authentication scheme, allowing user identity to be established without having to send a password in plaintext over the network.
- (Topic 3)
While reviewing the result of scanning run against a target network you come across the following: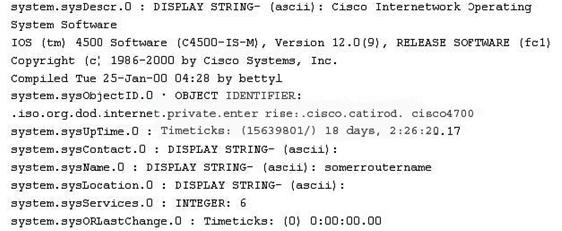
Which among the following can be used to get this output?
Correct Answer:D
SNMP lets you "read" information from a device. You make a query of the server (generally known as the "agent"). The agent gathers the information from the host system and returns the answer to your SNMP client. It's like having a single interface for all
your informative Unix commands. Output like system.sysContact.0 is called a MIB.
- (Topic 7)
You are sniffing as unprotected WiFi network located in a JonDonalds Cybercafe with Ethereal to capture hotmail e-mail traffic. You see lots of people using their laptops browsing the web while snipping brewed coffee from JonDonalds. You want to sniff their email message traversing the unprotected WiFi network.
Which of the following ethereal filters will you configure to display only the packets with the hotmail messages?
Correct Answer:A
Each Hotmail message contains the tag Reply-To:<sender address> and “xxxx-xxx-xxx.xxxx.hotmail.com” in the received tag.
- (Topic 23)
Blane is a security analyst for a law firm. One of the lawyers needs to send out an email to a client but he wants to know if the email is forwarded on to any other recipients. The client is explicitly asked not to re-send the email since that would be a violation of the lawyer's and client's agreement for this particular case. What can Blane use to accomplish this?
Correct Answer:D