- (Topic 19)
SSL has been seen as the solution to several common security problems. Administrators will often make use of SSL to encrypt communication from point A to point B. Why do you think this could be a bad idea if there is an Intrusion Detection System deployed to monitor the traffic between point A and B?
Correct Answer:D
Because the traffic is encrypted, an IDS cannot understand it or evaluate the payload.
- (Topic 5)
When discussing passwords, what is considered a brute force attack?
Correct Answer:A
Brute force cracking is a time consuming process where you try every possible combination of letters, numbers, and characters until you discover a match.
- (Topic 15)
Bob reads an article about how insecure wireless networks can be. He gets approval from his management to implement a policy of not allowing any wireless devices on the network. What other steps does Bob have to take in order to successfully implement this? (Select 2 answer.)
Correct Answer:AD
If someone installs a access point and connect it to the network there is no way to find it unless you are constantly surveying the area for wireless devices. SNMP and firewalls can not prevent the installation of wireless devices on the corporate network.
- (Topic 4)
Which of the following statements about a zone transfer correct?(Choose three.
Correct Answer:ACE
Securing DNS servers should be a priority of the organization. Hackers obtaining DNS information can discover a wealth of information about an organization. This information can be used to further exploit the network.
- (Topic 23)
What type of Trojan is this?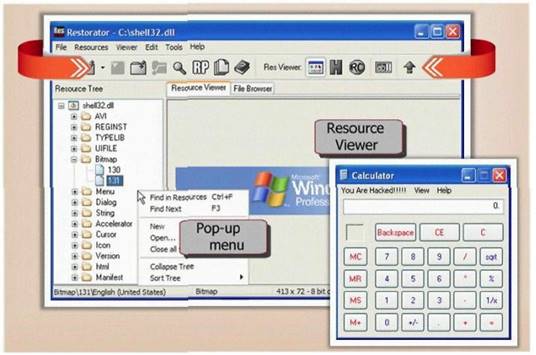
Correct Answer:C