- (Topic 8)
Which one of the following network attacks takes advantages of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
Correct Answer:A
The teardrop attack uses overlapping packet fragments to confuse a target system and cause the system to reboot or crash.
- (Topic 15)
In order to attack a wireless network, you put up an access point and override the signal of the real access point. As users send authentication data, you are able to capture it. What kind of attack is this?
Correct Answer:C
The definition of a Rogue access point is:1. A wireless access point (AP) installed by an employee without the consent of the IT department. Without the proper security configuration, users have exposed their company's network to the outside world.2. An access point (AP) set up by an attacker outside a facility with a wireless network. Also called an "evil twin," the rogue AP picks up beacons (signals that advertise its presence) from the company's legitimate AP and transmits identical beacons, which some client machines inside the building associate with.
- (Topic 23)
What is the correct command to run Netcat on a server using port 56 that spawns command shell when connected?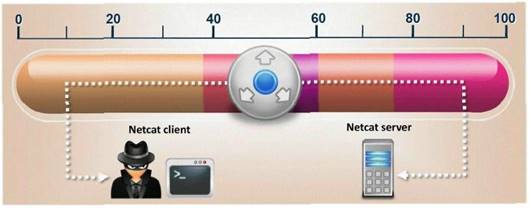
Correct Answer:D
- (Topic 4)
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab and is now ready for real world exploitation. He was able to effectively intercept communications between the two entities and establish credentials with both sides of the connections. The two remote ends of the communication never notice that Eric is relaying the information between the two.
What would you call this attack?
Correct Answer:B
A man-in-the-middle attack (MITM) is an attack in which an attacker is able to read, insert and modify at will, messages between two parties without either party knowing that the link between them has been compromised.
- (Topic 5)
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Correct Answer:B
When looking at an extracted LM hash, you will sometimes observe that the right most portion is always the same. This is padding that has been added to a password that is less than 8 characters long.