- (Topic 23)
In which location, SAM hash passwords are stored in Windows 7?
Correct Answer:A
- (Topic 23)
Joseph has just been hired on to a contractor company of the Department of Defense as their Senior Security Analyst. Joseph has been instructed on the company's strict security policies that have been implemented, and the policies that have yet to be put in place. Per the Department of Defense, all DoD users and the users of their contractors must use two- factor authentication to access their networks. Joseph has been delegated the task of researching and implementing the best two-factor authentication method for his company. Joseph's supervisor has told him that they would like to use some type of hardware device in tandem with a security or identifying pin number. Joseph's company has already
researched using smart cards and all the resources needed to implement them, but found the smart cards to not be cost effective. What type of device should Joseph use for two- factor authentication?
Correct Answer:D
- (Topic 19)
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application.
Which of the following strategies can be used to defeat detection by a network- based IDS application? (Choose the best answer)
Correct Answer:A
Certain types of encryption presents challenges to network-based intrusion detection and may leave the IDS blind to certain attacks, where a host-based IDS analyzes the data after it has been decrypted.
- (Topic 7)
What port number is used by Kerberos protocol?
Correct Answer:B
Kerberos traffic uses UDP/TCP protocol source and destination port 88.
- (Topic 4)
Exhibit: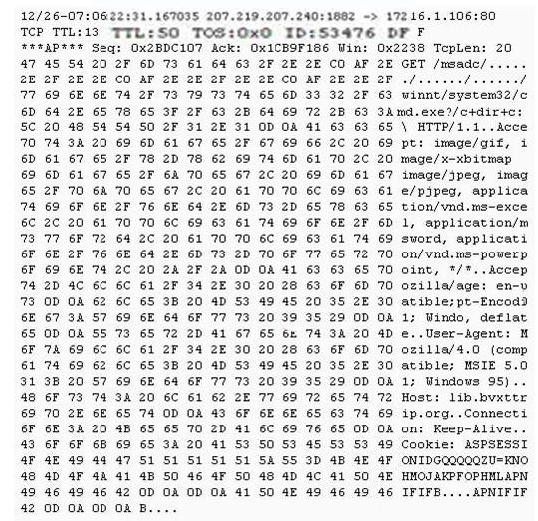
Study the following log extract and identify the attack.
Correct Answer:D
The “Get /msadc/……/……/……/winnt/system32/cmd.exe?” shows that a Unicode Directory Traversal Attack has been performed.