- (Topic 19)
You are the security administrator for a large network. You want to prevent attackers
from running any sort of traceroute into your DMZ and discover the internal structure of publicly accessible areas of the network.
How can you achieve this?
Correct Answer:D
When you run a traceroute to a target network address, you send a UDP packet with one time to live (TTL) to the target address. The first router this packet hits decreases the TTL to 0 and rejects the packet. Now the TTL for the packet is expired. The router sends back an ICMP message type 11 (Exceeded) code 0 (TTL--Exceeded) packet to your system with a source address. Your system displays the round-trip time for that first hop and sends out the next UDP packet with a TTL of 2.This process continues until you receive an ICMP message type 3 (Unreachable) code 3 (Port--Unreachable) from the destination system. Traceroute is completed when your machine receives a Port- Unreachable message.If you receive a message with three asterisks [* * *] during the traceroute, a router in the path doesn't return ICMP messages. Traceroute will continue to send UDP packets until the destination is reached or the maximum number of hops is exceeded.
- (Topic 16)
Virus Scrubbers and other malware detection program can only detect items that they are aware of. Which of the following tools would allow you to detect unauthorized changes or modifications of binary files on your system by unknown malware?
Correct Answer:A
Programs like Tripwire aids system administrators and users in monitoring a designated set of files for any changes. Used with system files on a regular (e.g., daily) basis, Tripwire can notify system administrators of corrupted or tampered files, so damage control measures can be taken in a timely manner.
- (Topic 19)
Exhibit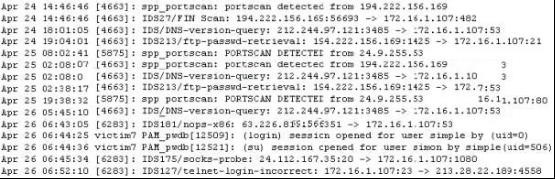
Study the log given in the exhibit,
Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
Correct Answer:C
According to the exhibit, the question is regarding the DNS Zone Transfer. Since Zone Transfers are done with TCP port 53, you should not allow this connect external to you organization.
- (Topic 19)
You may be able to identify the IP addresses and machine names for the firewall, and the names of internal mail servers by:
Correct Answer:C
- (Topic 3)
You have initiated an active operating system fingerprinting attempt with nmap against a target system:
[root@ceh NG]# /usr/local/bin/nmap -sT -O 10.0.0.1
Starting nmap 3.28 ( www.insecure.org/nmap/) at 2003-06-18 19:14 IDT Interesting ports on 10.0.0.1:
(The 1628 ports scanned but not shown below are in state: closed) Port State Service
21/tcp filtered ftp 22/tcp filtered ssh 25/tcp open smtp 80/tcp open http 135/tcp open loc-srv
139/tcp open netbios-ssn 389/tcp open LDAP 443/tcp open https 465/tcp open smtps 1029/tcp open ms-lsa 1433/tcp open ms-sql-s
2301/tcp open compaqdiag 5555/tcp open freeciv 5800/tcp open vnc-http 5900/tcp open vnc 6000/tcp filtered X11
Remote operating system guess: Windows XP, Windows 2000, NT4 or 95/98/98SE Nmap run completed -- 1 IP address (1 host up) scanned in 3.334 seconds
Using its fingerprinting tests nmap is unable to distinguish between different groups of Microsoft based operating systems - Windows XP, Windows 2000, NT4 or 95/98/98SE.
What operating system is the target host running based on the open ports shown above?
Correct Answer:D
The system is reachable as an active directory domain controller (port 389, LDAP)