- (Topic 5)
Michael is the security administrator for the for ABC company. Michael has been charged with strengthening the company’s security policies, including its password policies. Due to certain legacy applications. Michael was only able to enforce a password group policy in Active Directory with a minimum of 10 characters. He has informed the company’s employes, however that the new password policy requires that everyone must have complex passwords with at least 14 characters. Michael wants to ensure that everyone is using complex passwords that meet the new security policy requirements. Michael has just logged on to one of the network’s domain controllers and is about to run the following command:
What will this command accomplish?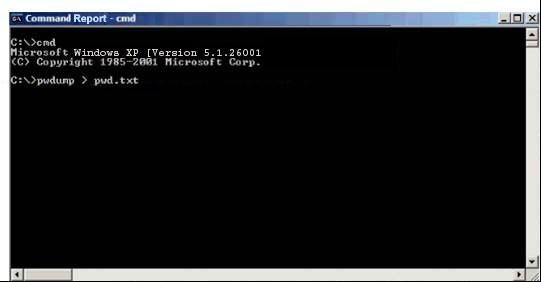
Correct Answer:A
Pwdump is a hack tool that is used to grab Windows password hashes from a remote Windows computer. Pwdump > pwd.txt will redirect the output from pwdump to a text file named pwd.txt
- (Topic 5)
LAN Manager passwords are concatenated to 14 bytes and split in half. The two halves are hashed individually. If the password is 7 characters or less, than the second half of the hash is always:
Correct Answer:A
A problem with LM stems from the total lack of salting or cipher block chaining in the hashing process. To hash a password the first 7 bytes of it are transformed into an 8 byte odd parity DES key. This key is used to encrypt the 8 byte string "KGS!@". Same thing happens with the second part of the password. This lack of salting creates two interesting consequences. Obviously this means the password is always stored in the same way, and just begs for a typical lookup table attack. The other consequence is that it is easy to tell if a password is bigger than 7 bytes in size. If not, the last 7 bytes will all be null and will result in a constant DES hash of 0xAAD3B435B51404EE.
- (Topic 2)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
(Note: The student is being tested on concept learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dumo.)
05/20-17:06:45.061034 192.160.13.4:31337 -> 172.16.1.101:1
TCP TTL:44 TOS:0x10 ID:242
***FRP** Seq: 0XA1D95 Ack: 0x53 Win: 0x400
.
.
.
05/20-17:06:58.685879 192.160.13.4:31337 -> 172.16.1.101:1024
TCP TTL:44 TOS:0x10 ID:242
***FRP** Seg: 0XA1D95 Ack: 0x53 Win: 0x400
What is odd about this attack? (Choose the most appropriate statement)
Correct Answer:B
Port 31337 is normally used by Back Orifice. Note that 31337 is hackers spelling of ‘elite’, meaning ‘elite hackers’.
- (Topic 2)
Which of the following tools are used for footprinting?(Choose four.
Correct Answer:ABCD
All of the tools listed are used for footprinting except Cheops.
- (Topic 5)
Which of the following LM hashes represent a password of less than 8 characters? (Select 2)
Correct Answer:BE
Notice the last 8 characters are the same