- (Topic 23)
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from this kind of response?
Correct Answer:A
- (Topic 23)
You generate MD5 128-bit hash on all files and folders on your computer to keep a baseline check for security reasons?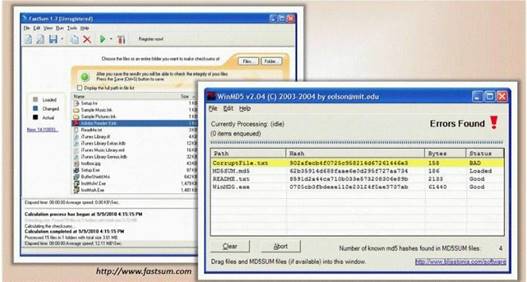
What is the length of the MD5 hash?
Correct Answer:C
- (Topic 23)
Syslog is a standard for logging program messages. It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.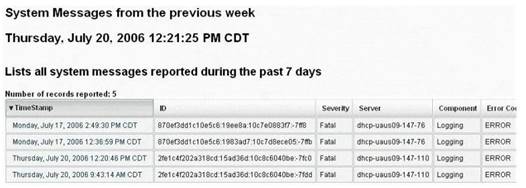
What default port Syslog daemon listens on?
Correct Answer:D
- (Topic 23)
This method is used to determine the Operating system and version running on a remote target system. What is it called?
Correct Answer:B
- (Topic 18)
You have just installed a new Linux file server at your office. This server is going to be used by several individuals in the organization, and unauthorized personnel must not be able to modify any data.
What kind of program can you use to track changes to files on the server?
Correct Answer:C
System Integrity Verifiers like Tripwire aids system administrators and users
in monitoring a designated set of files for any changes. Used with system files on a regular (e.g., daily) basis, Tripwire can notify system administrators of corrupted or tampered files, so damage control measures can be taken in a timely manner.