Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers?
Correct Answer:A
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.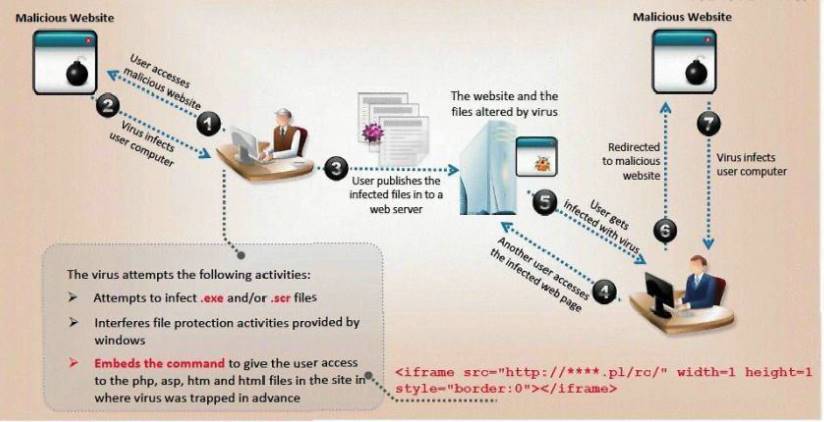
Here is a section of the Virus code: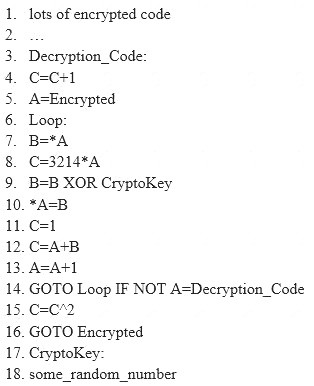
What is this technique called?
Correct Answer:A
You just set up a security system in your network. In what kind of system would you find the following string of characters used as a rule within its configuration? alert tcp any any -> 192.168.100.0/24 21 (msg: ““FTP on the network!””;)
Correct Answer:D
What does the following command in netcat do? nc -l -u -p55555 < /etc/passwd
Correct Answer:C
Which of the following is an extremely common IDS evasion technique in the web world?
Correct Answer:C