How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Correct Answer:B
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
Correct Answer:A
Take a look at the following attack on a Web Server using obstructed URL: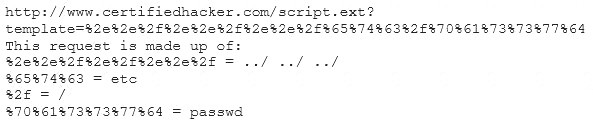
How would you protect from these attacks?
Correct Answer:B
What is the purpose of a demilitarized zone on a network?
Correct Answer:B
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
Correct Answer:C