Which of the following is the least-likely physical characteristic to be used in biometric control that supports a large company?
Correct Answer:C
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c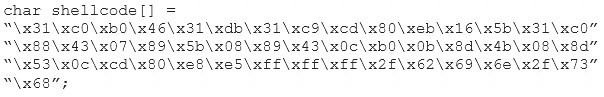
What is the hexadecimal value of NOP instruction?
Correct Answer:D
As a securing consultant, what are some of the things you would recommend to a company to ensure DNS security?
Correct Answer:BCDE
is a set of extensions to DNS that provide the origin authentication of DNS data to DNS clients (resolvers) so as to reduce the threat of DNS poisoning, spoofing, and similar types of attacks.
Correct Answer:A
Hackers often raise the trust level of a phishing message by modeling the email to look similar to the internal email used by the target company. This includes using logos, formatting, and names of the target company. The phishing message will often use the name of the company CEO, President, or Managers. The time a hacker spends performing research to locate this information about a company is known as?
Correct Answer:C