What is a principle of Infrastructure as Code?
Correct Answer:B
Refer to the exhibit.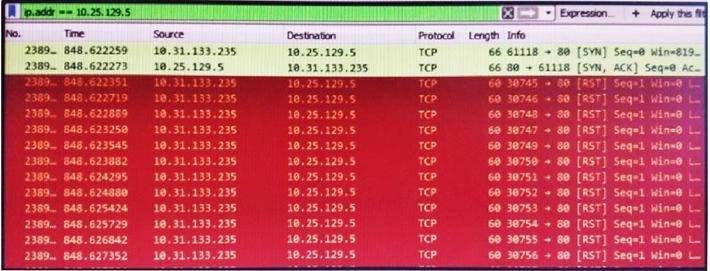
What is occurring in this packet capture?
Correct Answer:B
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high. Which step should be taken to continue the investigation?
Correct Answer:A
Refer to the exhibit.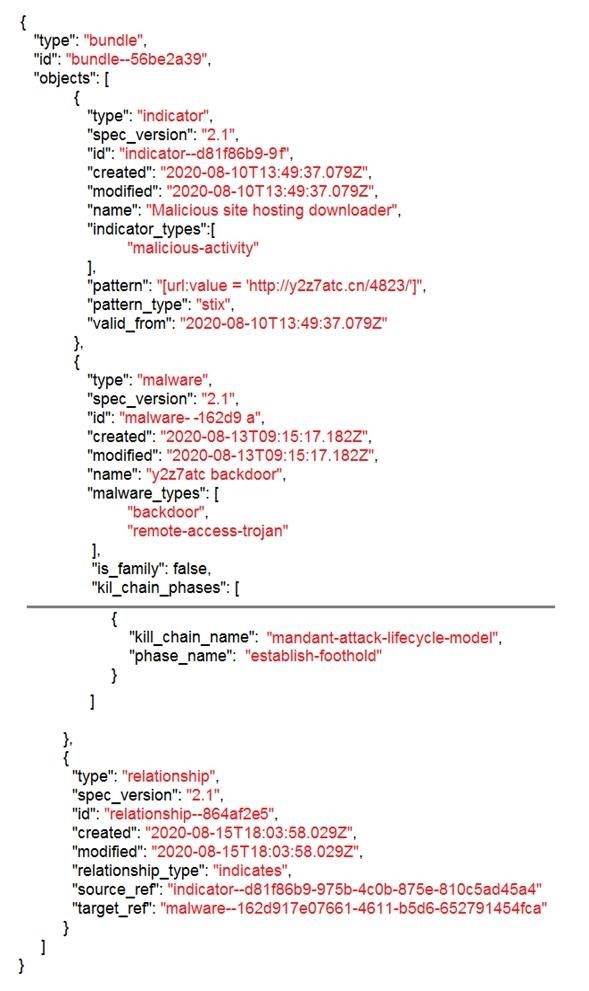
Which indicator of compromise is represented by this STIX?
Correct Answer:C
An engineer receives a report that indicates a possible incident of a malicious insider sending company information to outside parties. What is the first action the engineer must take to determine whether an incident has occurred?
Correct Answer:C