- (Exam Topic 3)
Which Python snippet should be used to store the devices data structure in a JSON file?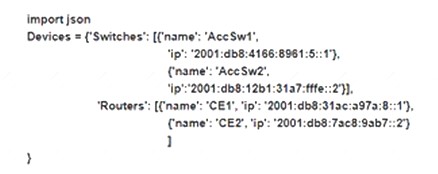
A)
B)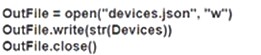
C)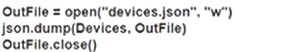
D)
Correct Answer:A
- (Exam Topic 2)
Which threat defence mechanism, when deployed at the network perimeter, protects against zero-day attacks?
Correct Answer:C
Reference: https://www.cisco.com/c/en/us/products/collateral/security/amp-appliances/datasheet-c78-733182.h analysis and sandboxing: Secure Malware Analytics’ highly secure environment helps you execute, analyze,
and test malware behavior to discover previously unknown ZERO-DAY threats. The integration of Secure Malware Analytics’ sandboxing technology into Malware Defense results in more dynamic analysis checked against a larger set of behavioral indicators. “
- (Exam Topic 2)
An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button under the Layer 3 Security options for Web Policy. Which device presents the web authentication for the WLAN?
Correct Answer:B
“The next step is to configure the WLC for the Internal web authentication. Internal web authentication is the defaultweb authentication type on WLCs.”
In step 4 of the link above, we will configure Security as described in this question. Therefore we can deduce thisconfiguration is for Internal web authentication.
This paragraph was taken from the link
https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlan-security/69340-web-auth-config.html#c5 :
- (Exam Topic 2)
Refer to the exhibit.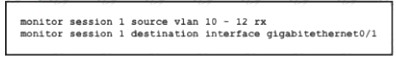
An engineer must configure a SPAN session. What is the effect of the configuration?
Correct Answer:C
- (Exam Topic 1)
Which command set configures RSPAN to capture outgoing traffic from VLAN 3 on interface GigabitEthernet 0/3 while ignoring other VLAN traffic on the same interface?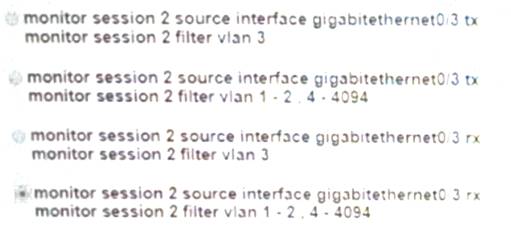
Correct Answer:A