- (Exam Topic 3)
An administrator is configuring NETCONF using the following XML string. What must the administrator end the request with?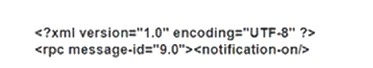
Correct Answer:A
- (Exam Topic 3)
An engineer must configure a new loopback Interface on a router and advertise the interface as a fa4 in OSPF. Which command set accomplishes this task?
A)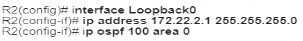
B)
C)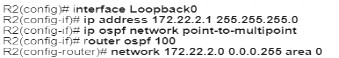
D)
Correct Answer:A
 Step 1. Create the loopback interface using the interface loopback number global configuration command.
Step 1. Create the loopback interface using the interface loopback number global configuration command. Step 2. Add a description. Although optional, it is a necessary component for documenting a network.
Step 2. Add a description. Although optional, it is a necessary component for documenting a network. Step 3. Configure the IP address.
Step 3. Configure the IP address.
For example, the following commands configure a loopback interface of the R1 router shown in (shown earlier in the chapter):
R1# configure terminal
R1(config)# interface loopback 0
R1(config-if)# ip address 10.0.0.1 255.255.255.0
R1(config-if)# exit
R1(config)#
- (Exam Topic 2)
An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
Correct Answer:B
Ransomware are malicious software that locks up critical resources of the users. Ransomware uses well-established public/private key cryptography which leaves the only way of recovering the files being the payment of the ransom, or restoring
files from backups.
Cisco Advanced Malware Protection (AMP) for Endpoints Malicious Activity Protection (MAP) engine defends your endpoints by monitoring the system and identifying processes that exhibit malicious activities when they execute and stops them from running. Because the MAP engine detects threats by observing the behavior of the process at run time, it can generically determine if a system is under attack by a new variant of ransomware or malware that may have eluded other security products and detection technology, such as legacy signature-based malware detection. The first release of the MAP engine targets identification, blocking, and quarantine of ransomware attacks on the endpoint.
Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/ampfor- endpoints/white-paper-c11-740980.pdf
- (Exam Topic 4)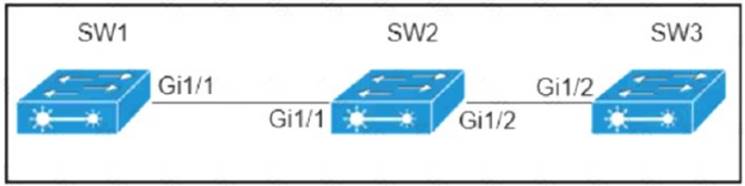
Company policy restricts VLAN 10 to be allowed only on SW1 and SW2. All other VLANs can be on all three switches. An administrator has noticed that VLAN 10 has propagated to SW3. Which configuration corrects the issue?
Correct Answer:C
- (Exam Topic 4)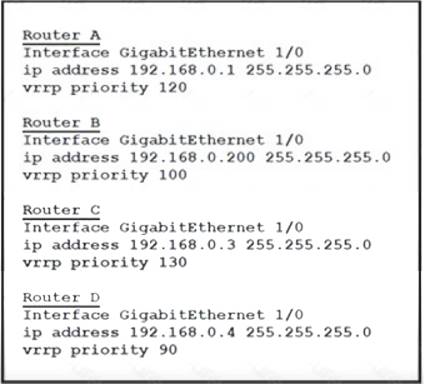
Refer to the exhibit. Which router is elected as the VRRP primary virtual router?
Correct Answer:C