On which part of the IT environment does DevSecOps focus?
Correct Answer:A
Refer to the exhibit.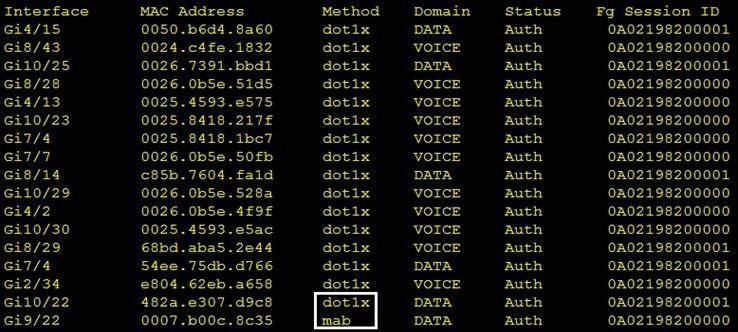
Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
Correct Answer:B
Refer to the exhibit.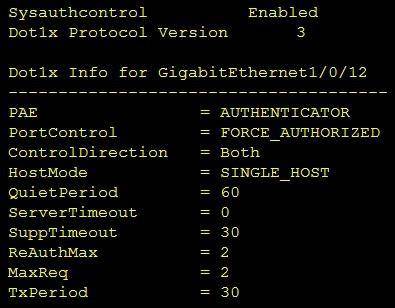
Which command was used to display this output?
Correct Answer:A
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/config-ieee-802x-pba.html
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options?
Correct Answer:D
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01011.html
DRAG DROP
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
[MISSING]
Solution:
[MISSING]
Does this meet the goal?
Correct Answer:A