An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
Correct Answer:AC
A network operations team is using the cloud to automate some of their managed customer and branch locations. They require that all of their tooling be ephemeral by design and that the entire automation environment can be recreated without manual commands. Automation code and configuration state will be stored in git for change control and versioning. The engineering high-level plan is to use VMs in a cloud-provider environment then configure open source tooling onto these VMs to poll, test, and configure the remote devices, as well as deploy the tooling itself.
Which configuration management and/or automation tooling is needed for this solution?
Correct Answer:B
DRAG DROP
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.
Select and Place: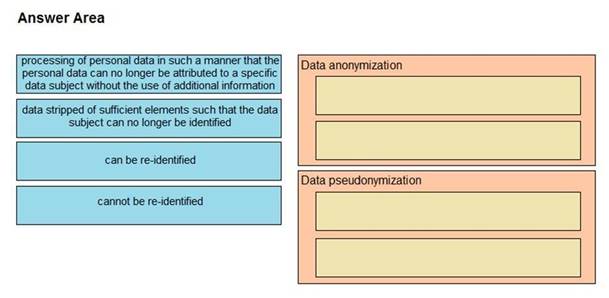
Solution: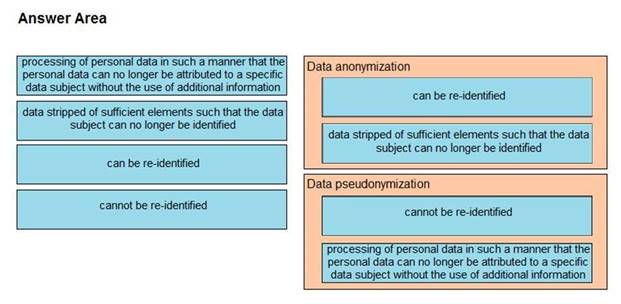
Does this meet the goal?
Correct Answer:A
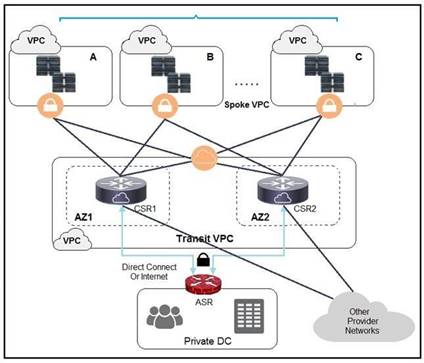
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)
Correct Answer:BD
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority. Which approach must be taken to secure API keys and passwords?
Correct Answer:D