- (Exam Topic 5)
You need to ensure receipt processing occurs correctly. What should you do?
Correct Answer:B
You can create a snapshot of a blob. A snapshot is a read-only version of a blob that's taken at a point in time. Once a snapshot has been created, it can be read, copied, or deleted, but not modified. Snapshots provide a way to back up a blob as it appears at a moment in time.
Scenario: Processing is performed by an Azure Function that uses version 2 of the Azure Function runtime. Once processing is completed, results are stored in Azure Blob Storage and an Azure SQL database. Then, an email summary is sent to the user with a link to the processing report. The link to the report must remain valid if the email is forwarded to another user.
Reference:
https://docs.microsoft.com/en-us/rest/api/storageservices/creating-a-snapshot-of-a-blob
- (Exam Topic 7)
Your company is developing an Azure API.
You need to implement authentication for the Azure API. You have the following requirements:  All API calls must be secure.
All API calls must be secure. Callers to the API must not send credentials to the API.
Callers to the API must not send credentials to the API.
Which authentication mechanism should you use?
Correct Answer:C
Use the authentication-managed-identity policy to authenticate with a backend service using the managed identity of the API Management service. This policy essentially uses the managed identity to obtain an access token from Azure Active Directory for accessing the specified resource. After successfully obtaining the token, the policy will set the value of the token in the Authorization header using the Bearer scheme.
Reference:
https://docs.microsoft.com/bs-cyrl-ba/azure/api-management/api-management-authentication-policies
- (Exam Topic 7)
A company is developing a gaming platform. Users can join teams to play online and see leaderboards that include player statistics. The solution includes an entity named Team.
You plan to implement an Azure Redis Cache instance to improve the efficiency of data operations for entities that rarely change.
You need to invalidate the cache when team data is changed.
How should you complete the code? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.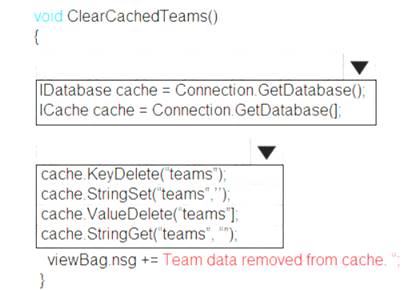
Solution:
Box 1: IDatabase cache = connection.GetDatabase();
Connection refers to a previously configured ConnectionMultiplexer.
Box 2: cache.StringSet("teams",")
To specify the expiration of an item in the cache, use the TimeSpan parameter of StringSet. cache.StringSet("key1", "value1", TimeSpan.FromMinutes(90));
References:
https://azure.microsoft.com/sv-se/blog/lap-around-azure-redis-cache-preview/
Does this meet the goal?
Correct Answer:A
- (Exam Topic 7)
You are preparing to deploy a medical records application to an Azure virtual machine (VM). The application will be deployed by using a VHD produced by an on-premises build server.
You need to ensure that both the application and related data are encrypted during and after deployment to Azure.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.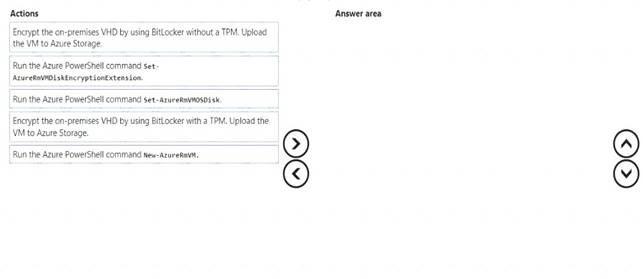
Solution:
Step 1: Encrypt the on-premises VHD by using BitLocker without a TPM. Upload the VM to Azure Storage Step 2: Run the Azure PowerShell command Set-AzureRMVMOSDisk
To use an existing disk instead of creating a new disk you can use the Set-AzureRMVMOSDisk command. Example:
$osDiskName = $vmname+'_osDisk'
$osDiskCaching = 'ReadWrite'
$osDiskVhdUri = "https://$stoname.blob.core.windows.net/vhds/"+$vmname+"_os.vhd"
$vm = Set-AzureRmVMOSDisk -VM $vm -VhdUri $osDiskVhdUri -name $osDiskName -Create Step 3: Run the Azure PowerShell command Set-AzureRmVMDiskEncryptionExtension
Use the Set-AzVMDiskEncryptionExtension cmdlet to enable encryption on a running IaaS virtual machine in Azure.
Incorrect:
Not TPM: BitLocker can work with or without a TPM. A TPM is a tamper resistant security chip on the system board that will hold the keys for encryption and check the integrity of the boot sequence and allows the most secure BitLocker implementation. A VM does not have a TPM.
References:
https://www.itprotoday.com/iaaspaas/use-existing-vhd-azurerm-vm
Does this meet the goal?
Correct Answer:A
- (Exam Topic 7)
You develop a serverless application using several Azure Functions. These functions connect to data from within the code.
You want to configure tracing for an Azure Function App project. You need to change configuration settings in the hostjson file. Which tool should you use?
Correct Answer:A
The function editor built into the Azure portal lets you update the function.json file and the code file for a function. The host.json file, which contains some runtime-specific configurations, is in the root folder of the function app.
References:
https://docs.microsoft.com/en-us/azure/azure-functions/functions-reference#fileupdate