No Installation Required, Instantly Prepare for the AZ-304 exam and please click the below link to start the AZ-304 Exam Simulator with a real AZ-304 practice exam questions.
Use directly our on-line AZ-304 exam dumps materials and try our Testing Engine to pass the AZ-304 which is always updated.
- (Exam Topic 3)
The developers at your company are building a containerized Python Django app.
You need to recommend platform to host the app. The solution must meet the following requirements:  Support autoscaling.
Support autoscaling. Support continuous deployment from an Azure Container Registry.
Support continuous deployment from an Azure Container Registry. Provide built-in functionality to authenticate app users by using Azure Active Directory (Azure AD). Which platform should you include in the recommendation?
Provide built-in functionality to authenticate app users by using Azure Active Directory (Azure AD). Which platform should you include in the recommendation?
Correct Answer:C
To keep up with application demands in Azure Kubernetes Service (AKS), you may need to adjust the number of nodes that run your workloads. The cluster autoscaler component can watch for pods in your cluster that can't be scheduled because of resource constraints. When issues are detected, the number of nodes in a node pool is increased to meet the application demand.
Azure Container Registry is a private registry for hosting container images. It integrates well with orchestrators like Azure Container Service, including Docker Swarm, DC/OS, and the new Azure Kubernetes service.
Moreover, ACR provides capabilities such as Azure Active Directory-based authentication, webhook support, and delete operations.
Reference:
https://docs.microsoft.com/en-us/azure/aks/cluster-autoscaler
https://medium.com/velotio-perspectives/continuous-deployment-with-azure-kubernetes-service-azurecontainer- registry-jenkins-ca337940151b
- (Exam Topic 1)
You need to recommend a solution to meet the database retention requirement. What should you recommend?
Correct Answer:A
- (Exam Topic 3)
A company named Contoso, Ltd- has an Azure Active Directory {Azure AD) tenant that uses the Basic license.
You plan to deploy two applications to Azure. The applications have the requirements shown in the following table.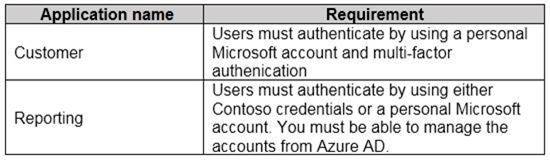
Which authentication strategy should you recommend for each application? To answer, drag the appropriate authentication strategies to the correct applications. Each authentication strategy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Solution:
Box 1: Azure AD V2.0 endpoint
Microsoft identity platform is an evolution of the Azure Active Directory (Azure AD) developer platform. It allows developers to build applications that sign in all Microsoft identities and get tokens to call Microsoft APIs, such as Microsoft Graph, or APIs that developers have built. The Microsoft identity platform consists of:
OAuth 2.0 and OpenID Connect standard-compliant authentication service that enables developers to authenticate any Microsoft identity, including:
Work or school accounts (provisioned through Azure AD)
Personal Microsoft accounts (such as Skype, Xbox, and Outlook.com) Social or local accounts (via Azure AD B2C)
Box 2: Azure AD B2C tenant
Azure Active Directory B2C provides business-to-customer identity as a service. Your customers use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.
Azure Active Directory B2C (Azure AD B2C) integrates directly with Azure Multi-Factor Authentication so that you can add a second layer of security to sign-up and sign-in experiences in your applications.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/active-directory-b2c-reference-mfa https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-overview
Does this meet the goal?
Correct Answer:A
- (Exam Topic 3)
You have an Azure App Service Web App that includes Azure Blob storage and an Azure SQL Database instance. The application is instrumented by using the Application Insights SDK.
You need to design a monitoring solution for the web app.
Which Azure monitoring services should you use? To answer, select the appropriate Azure monitoring services in the answer area.
NOTE: Each correct selection is worth one point.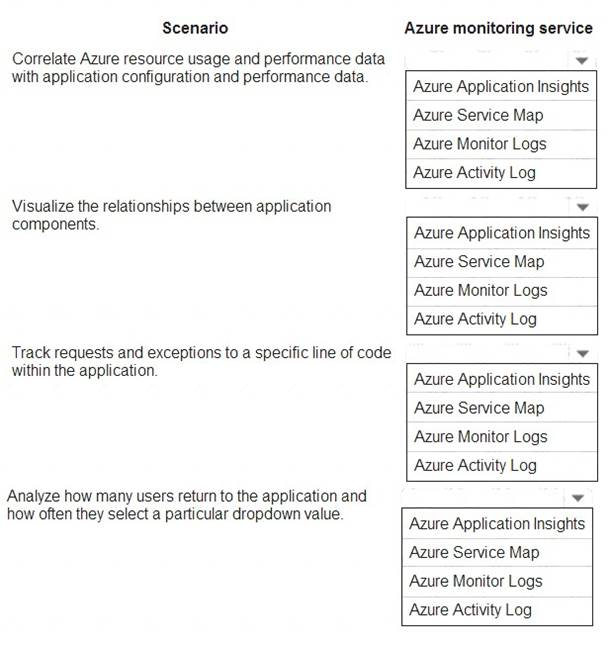
Solution:
* 1. Azure Monitor Log
* 2. Azure Application Insights (application map in App insights)
* 3. Azure Application Insights
* 4. Azure Application insights
https://docs.microsoft.com/en-us/azure/azure-monitor/app/app-map?tabs=net https://docs.microsoft.com/en-us/azure/azure-monitor/insights/service-map
Does this meet the goal?
Correct Answer:A
- (Exam Topic 3)
You are designing an Azure resource deployment that will use Azure Resource Manager templates. The deployment will use Azure Key Vault to store secrets.
You need to recommend a solution to meet the following requirements:
Prevent the IT staff that will perform the deployment from retrieving the secrets directly from Key Vault. Use the principle of least privilege.
Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Correct Answer:BD
B: To access a key vault during template deployment, set enabledForTemplateDeployment on the key vault to true.
D: The user who deploys the template must have the Microsoft.KeyVault/vaults/deploy/action permission for the scope of the resource group and key vault.
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/templates/key-vault-parameter https://docs.microsoft.com/en-us/azure/key-vault/general/overview-security