A customer has enabled LTPA as their authentication mechanism and has web resources that are not secured by proper security constraints. A system administrator is required to ensure that all web resources are secured.
How should the administrator accomplish this?
Correct Answer:A
Authenticate only when the URI is protected
The application server challenges the web client to provide authentication data when the web client accesses a Uniform Resource Identifier (URI) that is protected by a Java Platform, Enterprise Edition (Java EE) role. The authenticated identity is available only when the web client accesses a protected URI.
This option is the default Java EE web authentication behavior that is also available in previous releases of WebSphere® Application Server.
References: https://www.ibm.com/support/knowledgecenter/SSAW57_8.5.5/com.ibm.websphere.base.d oc/ae/usec_webauth.html
The computer where a federated node was running had a failure and cannot be recovered. A system administrator wants to recreate the node with the same configurations in another computer.
Which steps should the administrator execute in order to recover the damaged node?
Correct Answer:C
You can use the -asExistingNode option of the addNode command to recover and move nodes of a deployment manager. Using the -asExistingNode option, federate a new custom node to a deployment manager as an existing node. During federation, the product uses information in the deployment manager master configuration to transform the custom node into the existing node.
References: https://www.ibm.com/support/knowledgecenter/SSD28V_8.5.5/com.ibm.websphere.zseries
.doc/ae/tagt_addNode_asExistingNode.html
A system administrator has configured a network deployment cell containing multiple nodes and global security enabled with an LDAP repository. To increase capacity, the administrator needs to add additional nodes to the cell. After adding the nodes by using both scripts and the Integrated Solutions Console (ISC), the administrator examines the System.out log for the deployment manager and notices the following message: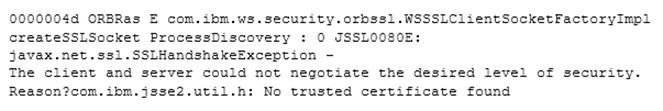
How can the administrator resolve this problem?
Correct Answer:B
When nodes are added while LDAP security is enabled, the following exception is generated in the deployment manager System.out log under certain circumstances. If this happens, restart the deployment manager to resolve the problem.
0000004d ORBRas E com.ibm.ws.security.orbssl.WSSSLClientSocketFactoryImpl createSSLSocket ProcessDiscovery : 0 JSSL0080E: javax.net.ssl.SSLHandshakeException -
The client and server could not negotiate the desired level of security. Reason?com.ibm.jsse2.util.h: No trusted certificate found
References: https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.0.0/com.ibm.websphere.nd. doc/info/ae/ae/tagt_svr_conf_nodes.html
A system administrator has deployed web applications to a clustered environment where database session persistence is configured. The administrator needs to improve the response time and the throughput.
How can the system administrator do this?
Correct Answer:B
The dynamic cache service improves performance by caching the output of servlets, commands, and JavaServer Pages (JSP) files. WebSphere Application Server consolidates several caching activities, including servlets, web services, and WebSphere commands, into one service called the dynamic cache. These caching activities work together to improve application performance and share many configuration parameters that are set in an application server’s dynamic cache service.
References: WebSphere Application Server V8.5 Administration and Configuration Guide for the Full Profile (July 2013), page 512
An EJB application posts a request message into a JMS destination and waits for a response message on a different JMS destination. To correlate the response message to the request message, the application uses the JMS correlationId of the message. The application waits up to five seconds for a response before timing out the request.
A Message Driven Bean (MDB) running on a different cluster is responsible for consuming the request message, process it and post a response message.
The destinations are defined in a Service Integration Bus (SIB) within the cell.
Intermittent timeout exceptions have occurred for the requester application. How can a system administrator correlate and analyze the debug information from both requester and consumer applications?
Correct Answer:C
Cross Component Trace (XCT) annotates the logs so that log entries that are related to a request that is serviced by more than one thread, process, or even server are identified as
belonging to the same unit of work. XCT helps identify the root cause of problems across components.
References: WebSphere Application Server V8.5 Administration and Configuration Guide for the Full Profile (July 2013), page 1091