An organization enables BYOD but wants to allow users to access the corporate email, calendar, and contacts from their devices. The data associated with the user’s accounts is sensitive, and therefore, the organization wants to comply with the following requirements:
Active full-device encryption Enabled remote-device wipe Blocking unsigned applications
Containerization of email, calendar, and contacts
Which of the following technical controls would BEST protect the data from attack or loss and meet the above requirements?
Correct Answer:B
Company ABC’s SAN is nearing capacity, and will cause costly downtimes if servers run out disk space. Which of the following is a more cost effective alternative to buying a new SAN?
Correct Answer:B
Storage-based data deduplication reduces the amount of storage needed for a given set of files. It is most effective in applications where many copies of very similar or even identical data are stored on a single disk.
It is common for multiple copies of files to exist on a SAN. By eliminating (deduplicating) repeated copies of the files, we can reduce the disk space used on the existing SAN. This solution is a cost effective alternative to buying a new SAN.
Incorrect Answers:
A: Multipathing enables multiple links to transfer the data to and from the SAN. This improves performance and link redundancy. However, it has no effect on the amount of data on the SAN. C: Snapshots would not reduce the amount of data stored on the SAN.
D: Replicating the data on the SAN to an offsite datacenter will not reduce the amount of data stored on the SAN. It would just create another copy of the data on the SAN in the offsite datacenter. References:
https://en.wikipedia.org/wiki/Data_deduplication
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company’s client-facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via SNMP from multiple IP addresses. Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
Correct Answer:A
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet: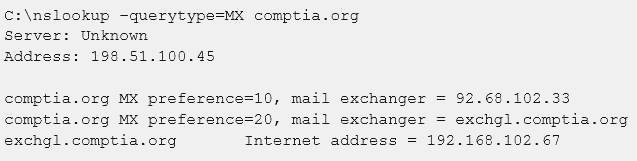
Which of the following should the penetration tester conclude about the command output?
Correct Answer:B
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.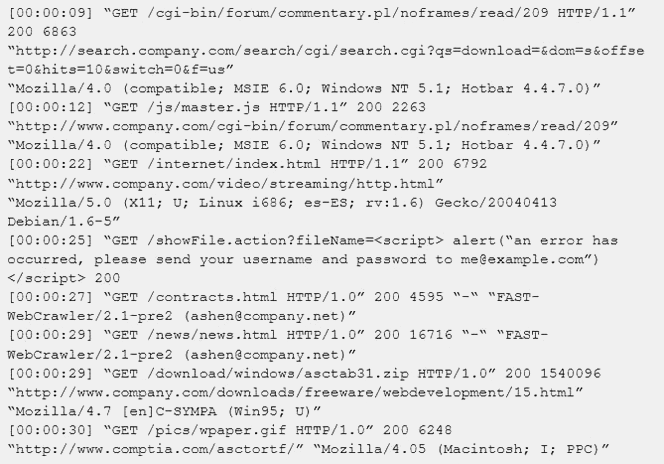
Which of the following types of attack vector did the penetration tester use?
Correct Answer:B