While investigating a security event, an analyst finds evidence that a user opened an email attachment from an unknown source. Shortly after the user opened the attachment, a group of servers experienced a large amount of network and resource activity. Upon investigating the servers, the analyst discovers the servers were encrypted by ransomware that is demanding payment within 48 hours or all data will be destroyed. The company has no response plans for ransomware.
Which of the following is the NEXT step the analyst should take after reporting the incident to the management team?
Correct Answer:C
A security engineer thinks the development team has been hard-coding sensitive environment variables in its code. Which of the following would BEST secure the company’s CI/CD pipeline?
Correct Answer:A
Reference: https://about.gitlab.com/blog/2021/04/09/demystifying-ci-cd-variables/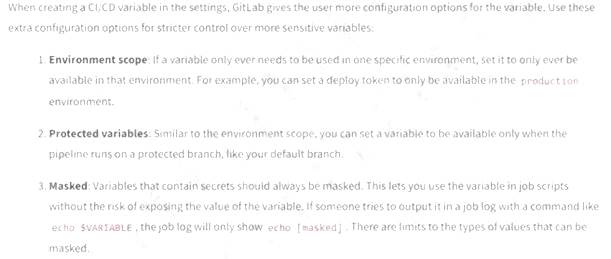
A developer wants to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users. Which of the following would be BEST for the developer to perform? (Choose two.)
Correct Answer:AB
A security engineer estimates the company’s popular web application experiences 100 attempted breaches per day. In the past four years, the company’s data has been breached two times.
Which of the following should the engineer report as the ARO for successful breaches?
Correct Answer:A
Reference: https://blog.netwrix.com/2020/07/24/annual-loss-expectancy-and-quantitative-risk-analysis/
A company wants to protect its intellectual property from theft. The company has already applied ACLs and DACs. Which of the following should the company use to prevent data theft?
Correct Answer:D