No Installation Required, Instantly Prepare for the CAS-005 exam and please click the below link to start the CAS-005 Exam Simulator with a real CAS-005 practice exam questions.
Use directly our on-line CAS-005 exam dumps materials and try our Testing Engine to pass the CAS-005 which is always updated.
A software company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?
Correct Answer:B
The most likely cause of the anti-malware alerts on customer workstations is unsecure bundled libraries. When developing and deploying new applications, it is common for developers to use third-party libraries. If these libraries are not properly vetted for security, they can introduce vulnerabilities or malicious code.
Why Unsecure Bundled Libraries?
✑ Third-Party Risks: Using libraries that are not secure can lead to malware infections if the libraries contain malicious code or vulnerabilities.
✑ Code Dependencies: Libraries may have dependencies that are not secure, leading to potential security risks.
✑ Common Issue: This is a frequent issue in software development where libraries are used for convenience but not properly vetted for security.
Other options, while relevant, are less likely to cause widespread anti-malware alerts:
✑ A. Misconfigured code commit: Could lead to issues but less likely to trigger anti- malware alerts.
✑ C. Invalid code signing certificate: Would lead to trust issues but not typically anti- malware alerts.
✑ D. Data leakage: Relevant for privacy concerns but not directly related to anti- malware alerts.
References:
✑ CompTIA SecurityX Study Guide
✑ "Securing Open Source Libraries," OWASP
✑ "Managing Third-Party Software Security Risks," Gartner Research
While reviewing recent modem reports, a security officer discovers that several employees were contacted by the same individual who impersonated a recruiter. Which of the following best describes this type of correlation?
Correct Answer:A
The situation where several employees were contacted by the same individual impersonating a recruiter best describes a spear-phishing campaign. Here??s why:
✑ Targeted Approach: Spear-phishing involves targeting specific individuals within an organization with personalized and convincing messages to trick them into divulging sensitive information or performing actions that compromise security.
✑ Impersonation: The use of impersonation, in this case, a recruiter, is a common tactic in spear-phishing to gain the trust of the targeted individuals and increase the likelihood of a successful attack.
✑ Correlated Contacts: The fact that several employees were contacted by the same individual suggests a coordinated effort to breach the organization??s security by targeting multiple points of entry through social engineering.
✑ References:
A security configure is building a solution to disable weak CBC configuration for remote access connections lo Linux systems. Which of the following should the security engineer modify?
Correct Answer:D
The sshd_config file is the main configuration file for the OpenSSH server. To disable weak CBC (Cipher Block Chaining) ciphers for SSH connections, the security engineer should modify the sshd_config file to update the list of allowed ciphers. This file typically contains settings for the SSH daemon, including which encryption algorithms are allowed.
By editing the /etc/ssh/sshd_config file and updating the Ciphers directive, weak ciphers can be removed, and only strong ciphers can be allowed. This change ensures that the
SSH server does not use insecure encryption methods.
References:
✑ CompTIA Security+ Study Guide
✑ OpenSSH manual pages (man sshd_config)
✑ CIS Benchmarks for Linux
A security operations engineer needs to prevent inadvertent data disclosure when encrypted SSDs are reused within an enterprise. Which of the following is the most secure way to achieve this goal?
Correct Answer:C
The most secure way to prevent inadvertent data disclosure when encrypted SSDs are reused is to securely delete the encryption keys used by the SSD. Without the encryption keys, the data on the SSD remains encrypted and is effectively unreadable, rendering any residual data useless. This method is more reliable and efficient than overwriting data multiple times or using other physical destruction methods.
References:
✑ CompTIA SecurityX Study Guide: Highlights the importance of managing encryption keys and securely deleting them to protect data.
✑ NIST Special Publication 800-88, "Guidelines for Media Sanitization": Recommends cryptographic erasure as a secure method for sanitizing encrypted storage devices.
A security analyst is reviewing the following log: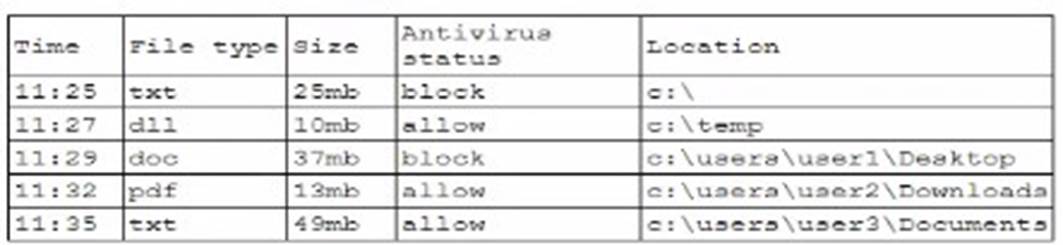
Which of the following possible events should the security analyst investigate further?
Correct Answer:B
Based on the log provided, the most concerning event that should be investigated further is
the presence of a text file containing passwords that were leaked. Here's why:
✑ Sensitive Information Exposure: A text file containing passwords represents a significant security risk, as it indicates that sensitive credentials have been exposed in plain text, potentially leading to unauthorized access.
✑ Immediate Threat: Password leaks can lead to immediate exploitation by attackers, compromising user accounts and sensitive data. This requires urgent investi