A Cisco switch is not accessible from the network. You need to view its running configuration.
Which out-of-band method can you use to access it?
Correct Answer:B

Out-of-band management
When a Cisco switch is not accessible from the network, the recommended out-of-band method to access its running configuration is through theconsole port. Out-of-band management involves accessing the network device through a dedicated management channel that is not part of the data network.The console port provides direct access to the switch??s Command Line Interface (CLI) without using the network, which is essential when the switch cannot be accessed remotely via the network12.
References:=
✑ Out-of-band (OOB) network interface configuration guidelines
✑ Out of band management configuration
=========================
If you have any more questions or need further assistance, feel free to ask!
DRAG DROP
Move each protocol from the list on the left to its correct example on the right.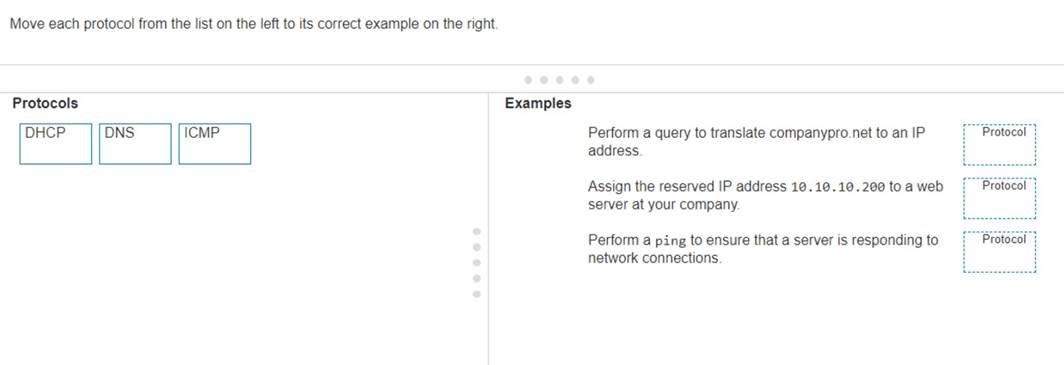
Solution:
The correct matching of the protocols to their examples is as follows:
✑ DHCP: Assign the reserved IP address 10.10.10.200 to a web server at your company.
✑ DNS: Perform a query to translate companypro.net to an IP address.
✑ ICMP: Perform a ping to ensure that a server is responding to network connections.
Here??s how each protocol corresponds to its example:
✑ DHCP (Dynamic Host Configuration Protocol)is used to assign IP addresses to devices on a network. In this case, DHCP would be used to assign the reserved IP address 10.10.10.200 to a web server.
✑ DNS (Domain Name System)is used to translate domain names into IP addresses.
Therefore, to translate companypro.net to an IP address, DNS would be utilized.
✑ ICMP (Internet Control Message Protocol)is used for sending error messages and operational information indicating success or failure when communicating with another IP address. An example of this is using the ping command to check if a server is responding to network connections.
These protocols are essential for the smooth operation of networks and the internet.
✑ Perform a query to translate companypro.net to an IP address.
✑ Assign the reserved IP address 10.10.10.200 to a web server at your company.
✑ Perform a ping to ensure that a server is responding to network connections.
✑ DNS (Domain Name System): DNS translates human-friendly domain names like "companypro.net" into IP addresses that computers use to identify each other on the network.
✑ DHCP (Dynamic Host Configuration Protocol): DHCP automatically assigns IP
addresses to devices on a network, ensuring that no two devices have the same IP address.
✑ ICMP (Internet Control Message Protocol): ICMP is used for diagnostic or control
purposes, and the ping command uses ICMP to test the reachability of a host on an IP network.
References:
✑ DNS Basics: What is DNS?
✑ DHCP Overview: What is DHCP?
✑ ICMP and Ping: Understanding ICMP
Does this meet the goal?
Correct Answer:A
DRAG DROP
Move each cloud computing service model from the list on the left to the correct example on the right
Note: You will receive partial credit for each correct answer.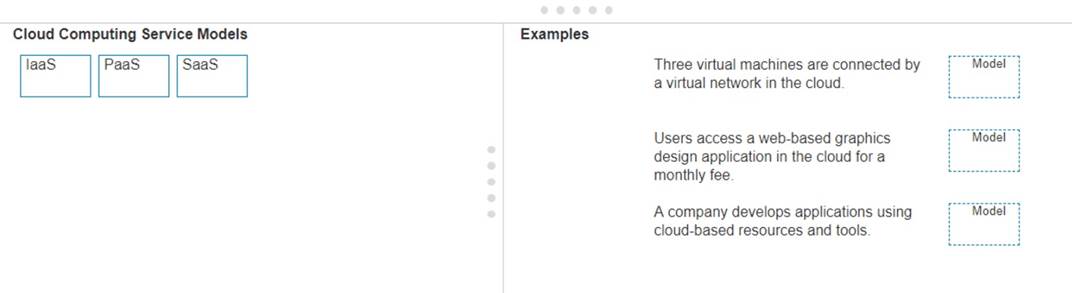
Solution:
✑ Three virtual machines are connected by a virtual network in the cloud.
✑ Users access a web-based graphics design application in the cloud for a monthly fee.
✑ A company develops applications using cloud-based resources and tools.
✑ IaaS (Infrastructure as a Service): Provides virtualized hardware resources that customers can use to build their own computing environments.
✑ PaaS (Platform as a Service): Offers a platform with tools and services to develop,
test, and deploy applications.
✑ SaaS (Software as a Service): Delivers fully functional applications over the internet that users can access and use without managing the underlying infrastructure.
References:
✑ Cloud Service Models: Understanding IaaS, PaaS, SaaS
✑ NIST Definition of Cloud Computing:NIST Cloud Computing
Does this meet the goal?
Correct Answer:A
DRAG DROP
Move each protocol from the list on the left to the correct TCP/IP model layer on the right. Note: You will receive partial credit for each correct match.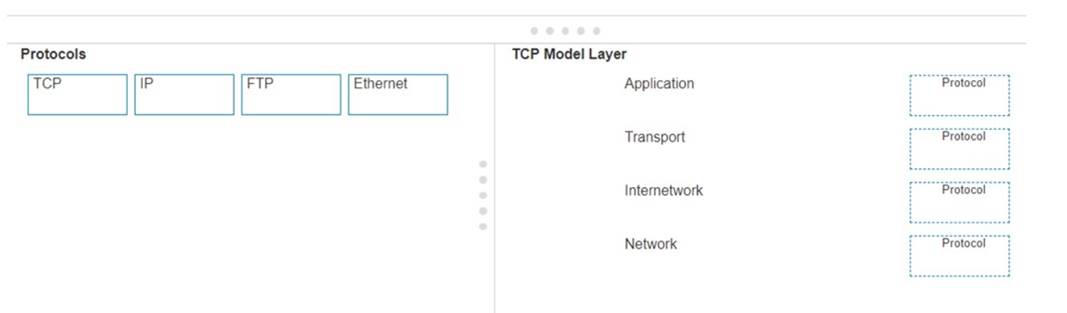
Solution:
Here??s how each protocol aligns with the correct TCP/IP model layer:
✑ TCP (Transmission Control Protocol): This protocol belongs to theTransportlayer, which is responsible for providing communication between applications on different hosts1.
✑ IP (Internet Protocol): IP is part of theInternetworklayer, which is tasked with routing packets across network boundaries to their destination1.
✑ FTP (File Transfer Protocol): FTP operates at theApplicationlayer, which supports application and end-user processes.It is used for transferring files over the network1.
✑ Ethernet: While not a protocol within the TCP/IP stack, Ethernet is associated with theNetwork Interfacelayer, which corresponds to the link layer of the TCP/IP model and is responsible for the physical transmission of data1.
The TCP/IP model layers are designed to work collaboratively to transmit data from one layer to another, with each layer having specific protocols that perform functions necessary for the data transmission process1.
✑ TCP:
✑ IP:
✑ FTP:
✑ Ethernet:
✑ Transport Layer: This layer is responsible for providing communication services directly to the application processes running on different hosts. TCP is a core protocol in this layer.
✑ Internetwork Layer: This layer is responsible for logical addressing, routing, and
packet forwarding. IP is the primary protocol for this layer.
✑ Application Layer: This layer interfaces directly with application processes and provides common network services. FTP is an example of a protocol operating in this layer.
✑ Network Layer: In the TCP/IP model, this layer includes both the data link and physical layers of the OSI model. Ethernet is a protocol used in this layer to define network standards and communication protocols at the data link and physical levels.
References:
✑ TCP/IP Model Overview: Cisco TCP/IP Model
✑ Understanding the TCP/IP Model: TCP/IP Layers
Does this meet the goal?
Correct Answer:A
Which protocol allows you to securely upload files to another computer on the internet?
Correct Answer:A
SFTP, or Secure File Transfer Protocol, is a protocol that allows for secure file transfer capabilities between networked hosts. It is a secure extension of the File Transfer Protocol (FTP). SFTP encrypts both commands and data, preventing passwords and sensitive information from being transmitted openly over the network. It is typically used for secure file transfers over the internet and is built on the Secure Shell (SSH) protocol1. References :=
•What Is SFTP? (Secure File Transfer Protocol)
•How to Use SFTP to Safely Transfer Files: A Step-by-Step Guide
•Secure File Transfers: Best Practices, Protocols And Tools
The Secure File Transfer Protocol (SFTP) is a secure version of the File Transfer Protocol (FTP) that uses SSH (Secure Shell) to encrypt all commands and data. This ensures that sensitive information, such as usernames, passwords, and files being transferred, are securely transmitted over the network.
•ICMP (Internet Control Message Protocol) is used for network diagnostics and is not designed for file transfer.
•NTP (Network Time Protocol) is used to synchronize clocks between computer systems and is not related to file transfer.
•HTTP (HyperText Transfer Protocol) is used for transmitting web pages over the internet and does not inherently provide secure file transfer capabilities.
Thus, the correct protocol that allows secure uploading of files to another computer on the internet is SFTP.
References :=
•Cisco Learning Network
•SFTP Overview (Cisco)