- (Topic 8)
What type of attack changes its signature and/or payload to avoid detection by antivirus programs?
Correct Answer:A
In computer terminology, polymorphic code is code that mutates while keeping the original algorithm intact. This technique is sometimes used by computer viruses, shellcodes and computer worms to hide their presence.
- (Topic 1)
Annie has just succeeded in stealing a secure cookie via a XSS attack. She is able to replay the cookie even while the session is invalid on the server. Why do you think this is possible?
Correct Answer:A
- (Topic 5)
Which security control role does encryption meet?
Correct Answer:A
- (Topic 4)
To reduce the attack surface of a system, administrators should perform which of the following processes to remove unnecessary software, services, and insecure configuration settings?
Correct Answer:C
- (Topic 1)
BankerFox is a Trojan that is designed to steal users' banking data related to certain banking entities.
When they access any website of the affected banks through the vulnerable Firefox 3.5 browser, the Trojan is activated and logs the information entered by the user. All the information entered in that website will be logged by the Trojan and transmitted to the attacker's machine using covert channel.
BankerFox does not spread automatically using its own means. It needs an attacking user's intervention in order to reach the affected computer.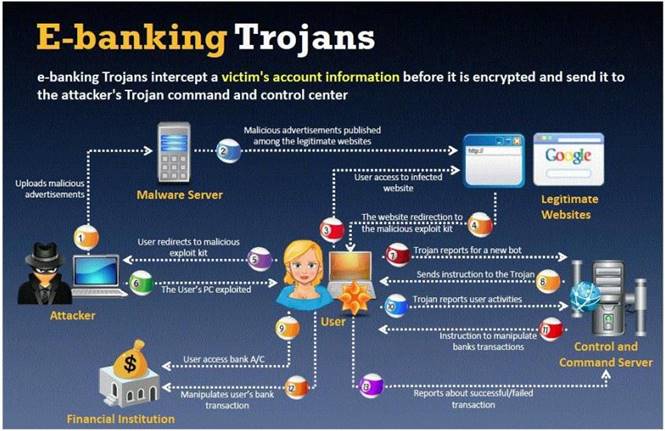
What is the most efficient way an attacker located in remote location to infect this banking Trojan on a victim's machine?
Correct Answer:E