- (Topic 4)
Which of the following is an example of an asymmetric encryption implementation?
Correct Answer:B
- (Topic 2)
How does a denial-of-service attack work?
Correct Answer:A
- (Topic 7)
A POP3 client contacts the POP3 server:
Correct Answer:B
POP is used to receive e-mail. SMTP is used to send e-mail.
- (Topic 1)
Attackers target HINFO record types stored on a DNS server to enumerate information. These are information records and potential source for reconnaissance. A network administrator has the option of entering host information specifically the CPU type and operating system when creating a new DNS record. An attacker can extract this type of information easily from a DNS server.
Which of the following commands extracts the HINFO record?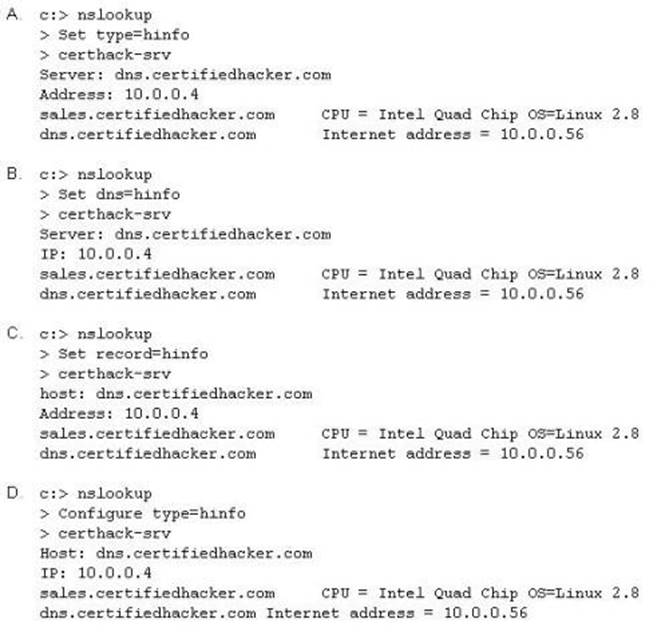
Correct Answer:A
- (Topic 4)
To send a PGP encrypted message, which piece of information from the recipient must the sender have before encrypting the message?
Correct Answer:B