- (Topic 5)
In the OSI model, where does PPTP encryption take place?
Correct Answer:C
- (Topic 8)
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application.
Which of the following strategies can be used to defeat detection by a network-based IDS application? (Choose the best answer)
Correct Answer:A
Certain types of encryption presents challenges to network-based intrusion detection and may leave the IDS blind to certain attacks, where a host-based IDS analyzes the data after it has been decrypted.
- (Topic 2)
What is the correct order of steps in CEH System Hacking Cycle?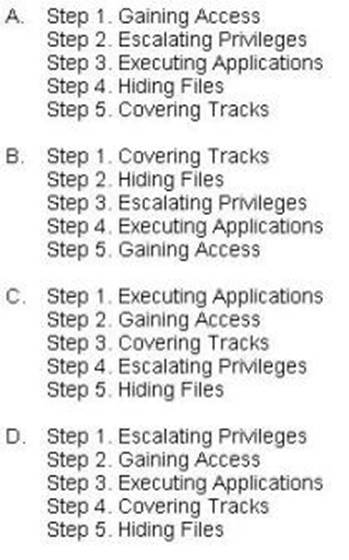
Correct Answer:A
- (Topic 1)
Stephanie works as a records clerk in a large office building in downtown Chicago. On Monday, she went to a mandatory security awareness class (Security5) put on by her company's IT department. During the class, the IT department informed all employees that everyone's Internet activity was thenceforth going to be monitored.
Stephanie is worried that her Internet activity might give her supervisor reason to write her up, or worse get her fired. Stephanie's daily work duties only consume about four hours of her time, so she usually spends the rest of the day surfing the web. Stephanie really enjoys surfing the Internet but definitely does not want to get fired for it.
What should Stephanie use so that she does not get in trouble for surfing the Internet?
Correct Answer:B
- (Topic 7)
Exhibit: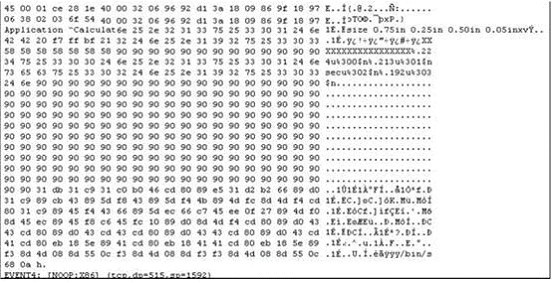
The following is an entry captured by a network IDS.You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?
Correct Answer:D
This log entry shows a hacker using a buffer overflow to fill the data buffer and trying to insert the execution of /bin/sh into the executable code part of the thread. It is probably an existing exploit that is used, or a directed attack with a custom built buffer overflow with the “payload” that launches the command shell.