- (Topic 1)
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, CWR. These flags have decimal numbers assigned to them:
FIN = 1
SYN = 2
RST = 4
PSH = 8
ACK = 16
URG = 32
ECE = 64
CWR = 128
Jason is the security administrator of ASPEN Communications. He analyzes some traffic using Wireshark and has enabled the following filters.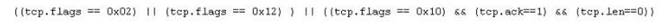
What is Jason trying to accomplish here?
Correct Answer:B
- (Topic 7)
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
Correct Answer:D
Sending a bogus email is one way to find out more about internal servers. Also, to gather additional IP addresses and learn how they treat mail.
- (Topic 5)
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106: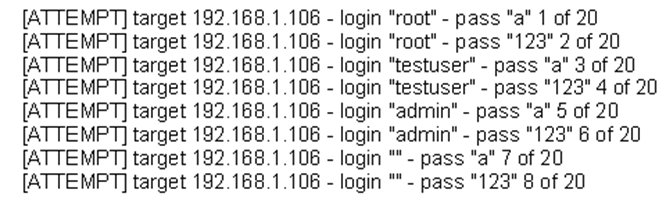
What is most likely taking place?
Correct Answer:B
- (Topic 4)
The intrusion detection system at a software development company suddenly generates multiple alerts regarding attacks against the company's external webserver, VPN concentrator, and DNS servers. What should the security team do to determine which alerts to check first?
Correct Answer:C
- (Topic 3)
Which of the following items of a computer system will an anti-virus program scan for viruses?
Correct Answer:A