- (Topic 3)
SOAP services use which technology to format information?
Correct Answer:C
- (Topic 4)
If the final set of security controls does not eliminate all risk in a system, what could be done next?
Correct Answer:C
- (Topic 4)
When using Wireshark to acquire packet capture on a network, which device would enable the capture of all traffic on the wire?
Correct Answer:A
- (Topic 7)
LM authentication is not as strong as Windows NT authentication so you may want to disable its use, because an attacker eavesdropping on network traffic will attack the weaker protocol. A successful attack can compromise the user's password. How do you disable LM authentication in Windows XP?
Correct Answer:C
http://support.microsoft.com/kb/299656
- (Topic 3)
You generate MD5 128-bit hash on all files and folders on your computer to keep a baseline check for security reasons?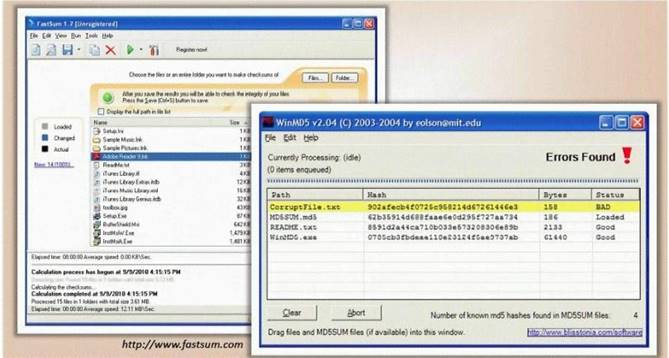
What is the length of the MD5 hash?
Correct Answer:A