- (Topic 5)
A tester is attempting to capture and analyze the traffic on a given network and realizes that the network has several switches. What could be used to successfully sniff the traffic on this switched network? (Choose three.)
Correct Answer:ABC
- (Topic 8)
Look at the following SQL query.
SELECT * FROM product WHERE PCategory='computers' or 1=1--' What will it return? Select the best answer.
Correct Answer:C
The 1=1 tells the SQL database to return everything, a simplified statement would be SELECT * FROM product WHERE 1=1 (which will always be true for all columns). Thus, this query will return all computers and everything else. The or 1=1 is a common test to see if a web application is vulnerable to a SQL attack.
- (Topic 7)
A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password. Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
Correct Answer:AB
As little information as possible should be given about a failed login attempt. Invalid username or password is not desirable.
- (Topic 3)
An attacker is attempting to telnet into a corporation's system in the DMZ. The attacker doesn't want to get caught and is spoofing his IP address. After numerous tries he remains unsuccessful in connecting to the system. The attacker rechecks that the target system is
actually listening on Port 23 and he verifies it with both nmap and hping2. He is still unable to connect to the target system. What could be the reason?
Correct Answer:C
- (Topic 1)
Attackers footprint target Websites using Google Hacking techniques. Google hacking is a term that refers to the art of creating complex search engine queries. It detects websites that are vulnerable to numerous exploits and vulnerabilities. Google operators are used to locate specific strings of text within the search results.
The configuration file contains both a username and a password for an SQL database. Most sites with forums run a PHP message base. This file gives you the keys to that forum, including FULL ADMIN access to the database. WordPress uses config.php that stores the database Username and Password.
Which of the below Google search string brings up sites with "config.php" files?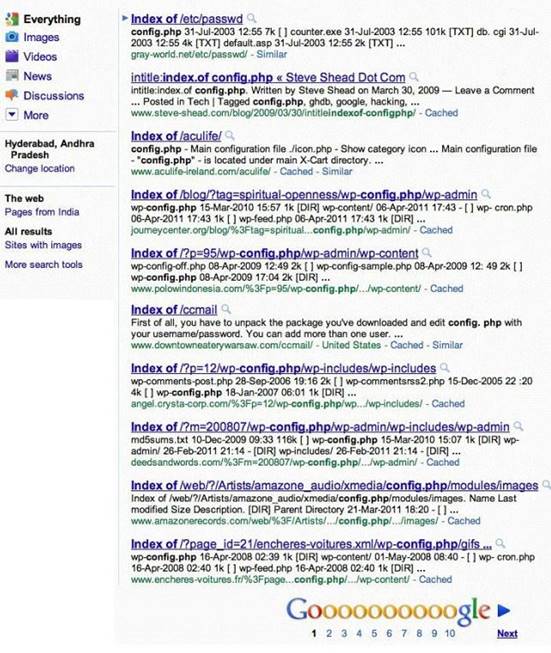
Correct Answer:C