- (Topic 1)
Dan is conducting penetration testing and has found a vulnerability in a Web Application which gave him the sessionID token via a cross site scripting vulnerability. Dan wants to replay this token. However, the session ID manager (on the server) checks the originating IP address as well. Dan decides to spoof his IP address in order to replay the sessionID. Why do you think Dan might not be able to get an interactive session?
Correct Answer:C
- (Topic 3)
What type of port scan is shown below?
Correct Answer:C
- (Topic 5)
Which of the following descriptions is true about a static NAT?
Correct Answer:D
- (Topic 2)
What type of encryption does WPA2 use?
Correct Answer:B
- (Topic 8)
Joe the Hacker breaks into XYZ’s Linux system and plants a wiretap program in order to sniff passwords and user accounts off the wire. The wiretap program is embedded as a Trojan horse in one of the network utilities. Joe is worried that network administrator might detect the wiretap program by querying the interfaces to see if they are running in promiscuous mode.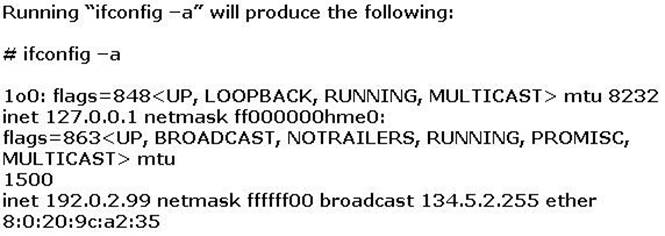
What can Joe do to hide the wiretap program from being detected by ifconfig command?
Correct Answer:C
The normal way to hide these rogue programs running on systems is the use crafted commands like ifconfig and ls.