- (Topic 8)
When referring to the Domain Name Service, what is denoted by a ‘zone’?
Correct Answer:B
A reasonable definition of a zone would be a portion of the DNS namespace where responsibility has been delegated.
- (Topic 4)
Data hiding analysis can be useful in
Correct Answer:B
- (Topic 6)
Which of the following Nmap commands would be used to perform a stack fingerprinting?
Correct Answer:A
This option activates remote host identification via TCP/IP fingerprinting. In other words, it uses a bunch of techniques to detect subtlety in the underlying operating system network stack of the computers you are scanning. It uses this information to create a "fingerprint" which it compares with its database of known OS fingerprints (the nmap-os- fingerprints file. to decide what type of system you are scanning.
- (Topic 3)
How do you defend against ARP Poisoning attack? (Select 2 answers)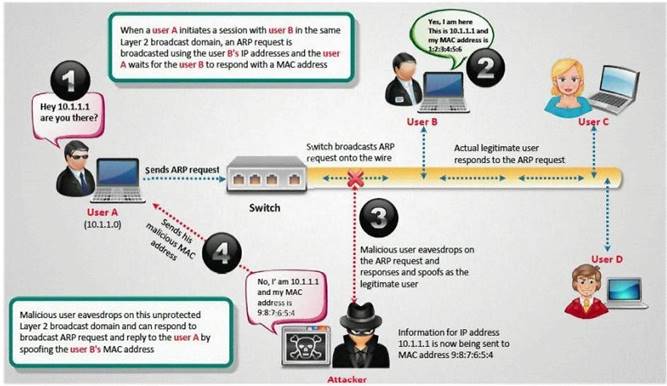
Correct Answer:AC
- (Topic 8)
802.11b is considered a protocol.
Correct Answer:C
802.11b is an insecure protocol. It has many weaknesses that can be used by a hacker.