- (Exam Topic 13)
Match the name of access control model with its associated restriction.
Drag each access control model to its appropriate restriction access on the right.
Solution: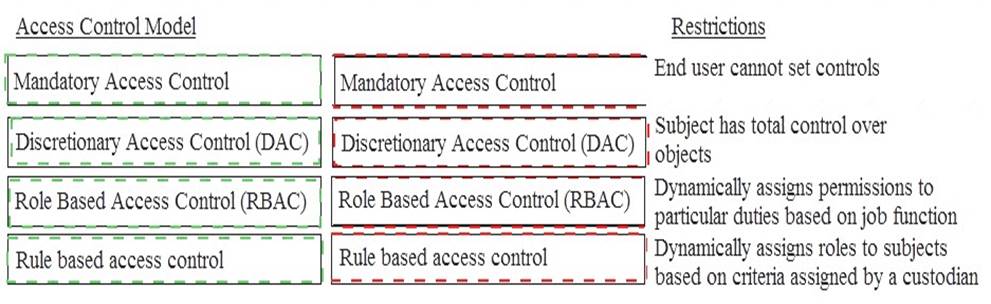
Does this meet the goal?
Correct Answer:A
- (Exam Topic 4)
An external attacker has compromised an organization’s network security perimeter and installed a sniffer onto an inside computer. Which of the following is the MOST effective layer of security the organization could have implemented to mitigate the attacker’s ability to gain further information?
Correct Answer:D
- (Exam Topic 9)
Which one of the following effectively obscures network addresses from external exposure when implemented on a firewall or router?
Correct Answer:A
- (Exam Topic 11)
Which security approach will BEST minimize Personally Identifiable Information (PII) loss from a data breach?
Correct Answer:B
- (Exam Topic 12)
What is the MOST important element when considering the effectiveness of a training program for Business Continuity (BC) and Disaster Recovery (DR)?
Correct Answer:B