- (Exam Topic 2)
An organization supports a large number of remote users. Which of the following is the BEST option to protect the data on the remote users1 laptops?
Correct Answer:A
- (Exam Topic 2)
An analyst wants to identify hosts that are connecting to the external FTP servers and what, if any, passwords are being used. Which of the following commands should the analyst use?
Correct Answer:A
- (Exam Topic 3)
An internally developed file-monitoring system identified the following except as causing a program to crash often: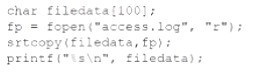
Which of the following should a security analyst recommend to fix the issue?
Correct Answer:A
- (Exam Topic 1)
A security analyst received an email with the following key: Xj3XJ3LLc
A second security analyst received an email with following key: 3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key that allows access to the company’s financial segment for maintenance. This is an example of:
Correct Answer:A
- (Exam Topic 3)
An incident response team detected malicious software that could have gained access to credit card data. The incident response team was able to mitigate significant damage and implement corrective actions. By having incident response mechanisms in place. Which of the following should be notified for lessons learned?
Correct Answer:D