- (Exam Topic 3)
An analyst is reviewing the output from some recent network enumeration activities. The following entry relates to a target on the network: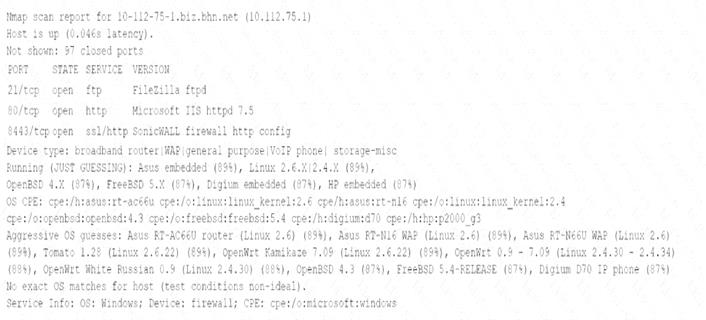
Based on the above output, which Of the following tools or techniques is MOST likely being used?
Correct Answer:A
- (Exam Topic 3)
An analyst receives artifacts from a recent Intrusion and is able to pull a domain, IP address, email address, and software version. When of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
Correct Answer:C
- (Exam Topic 1)
A security analyst wants to identify which vulnerabilities a potential attacker might initially exploit if the network is compromised Which of the following would provide the BEST results?
Correct Answer:D
- (Exam Topic 3)
While conoXicting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report: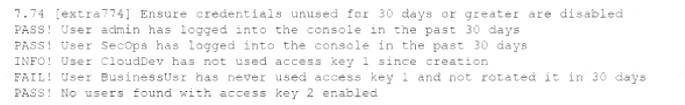
Based on the Prowler report, which of the following is the BEST recommendation?
Correct Answer:D
- (Exam Topic 1)
Which of the following policies would state an employee should not disable security safeguards, such as host firewalls and antivirus on company systems?
Correct Answer:D