A cyber-incident response analyst is investigating a suspected cryptocurrency miner on a company's server. Which of the following is the FIRST step the analyst should take?
Correct Answer:D
Joe, a penetration tester, used a professional directory to identify a network administrator and ID administrator for a client’s company. Joe then emailed the network administrator, identifying himself as the ID administrator, and asked for a current password as part of a security exercise. Which of the following techniques were used in this scenario?
Correct Answer:C
A network attack that is exploiting a vulnerability in the SNMP is detected. Which of the following should the cybersecurity analyst do FIRST?
Correct Answer:A
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC.
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
Correct Answer:B
A security analyst is reviewing the following log entries to identify anomalous activity: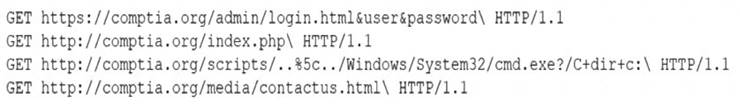
Which of the following attack types is occurring?
Correct Answer:A