- (Exam Topic 2)
A security analyst needs to identify possible threats to a complex system a client is developing. Which of the following methodologies would BEST address this task?
Correct Answer:C
- (Exam Topic 3)
Which of me following are reasons why consumer IoT devices should be avoided in an enterprise environment? (Select TWO)
Correct Answer:BD
- (Exam Topic 3)
Which of the following incident response components can identify who is the llaison between multiple lines of business and the pubic?
Correct Answer:C
- (Exam Topic 1)
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output: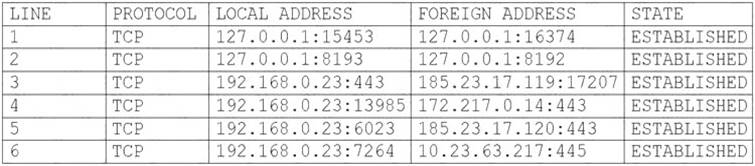
Which of the following lines indicates the computer may be compromised?
Correct Answer:D
- (Exam Topic 1)
A security analyst recently discovered two unauthorized hosts on the campus's wireless network segment from a man-m-the-middle attack .The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
Correct Answer:A