A company’s Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user’s activity session. Which of the following is the BEST technique to address the CISO’s concerns?
Correct Answer:A
While analyzing logs from a WAF, a cybersecurity analyst finds the following: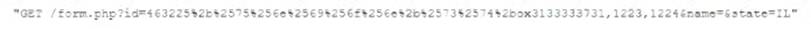
Which of the following BEST describes what the analyst has found?
Correct Answer:D
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior results in the industrial generators overheating and destabilizing the power supply.
Which of the following would BEST identify potential indicators of compromise?
Correct Answer:C
Which of the following is the MOST important objective of a post-incident review?
Correct Answer:A
A cybersecurity analyst needs to rearchitect the network using a firewall and a VPN server to achieve the highest level of security To BEST complete this task, the analyst should place the:
Correct Answer:B