- (Exam Topic 1)
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
Which of the following should the analyst review to find out how the data was exfilltrated?
Correct Answer:D
- (Exam Topic 1)
A security team wants to make SaaS solutions accessible from only the corporate campus Which of the following would BEST accomplish this goal?
Correct Answer:A
Reference: https://bluedot.io/library/what-is-geofencing/
- (Exam Topic 1)
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results: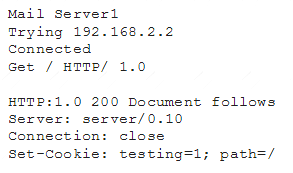
Which of the following describes the output of this scan?
Correct Answer:B
- (Exam Topic 3)
During routine monitoring a security analyst identified the following enterpnse network traffic: Packet capture output: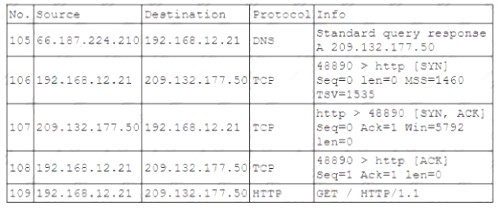
Which of the following BEST describes what the security analyst observed?
Correct Answer:C
- (Exam Topic 1)
As part of a review of modern response plans, which of the following is MOST important for an organization lo understand when establishing the breach notification period?
Correct Answer:D