- (Exam Topic 1)
Which of the following technologies can be used to house the entropy keys for disk encryption on desktops and laptops?
Correct Answer:A
- (Exam Topic 2)
While conducting a network infrastructure review, a security analyst discovers a laptop that is plugged into a core switch and hidden behind a desk.
The analyst sees the following on the laptop's screen: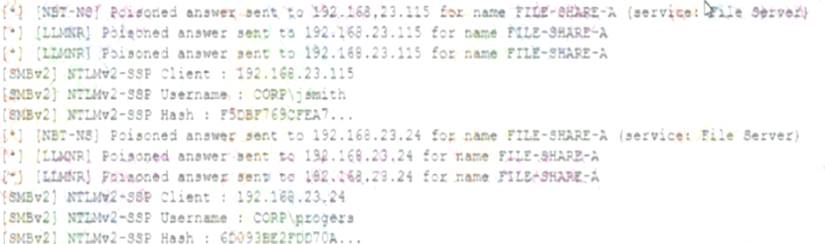
Which of the following is the BEST action for the security analyst to take?
Correct Answer:D
- (Exam Topic 1)
An organization suspects it has had a breach, and it is trying to determine the potential impact. The organization knows the following: The source of the breach is linked to an IP located in a foreign country.
The source of the breach is linked to an IP located in a foreign country.  The breach is isolated to the research and development servers.
The breach is isolated to the research and development servers. The hash values of the data before and after the breach are unchanged.
The hash values of the data before and after the breach are unchanged. The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
Correct Answer:BD
- (Exam Topic 1)
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integration intelligence into hunt operations?
Correct Answer:A
- (Exam Topic 1)
A cybersecurity analyst is supposing an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
Correct Answer:D